Lesson Contents
The firewall is the barrier between a trusted and untrusted network, often used between your LAN and WAN. It’s typically placed in the forwarding path so that all packets have to be checked by the firewall, where we can drop or permit them. Here’s an example:
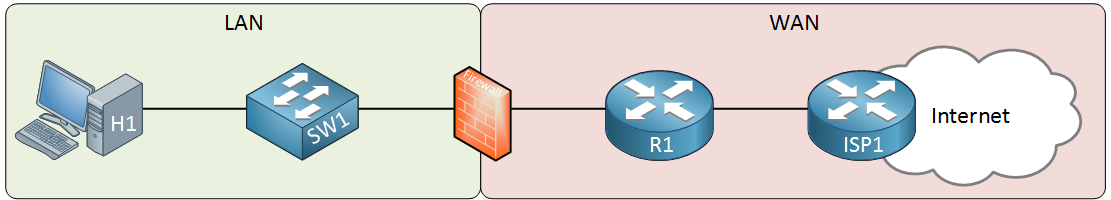
Above we have our LAN that has a host computer and a switch. On the right side, there’s a router that is connected to the ISP which offers Internet connectivity. The firewall sits in between to protect our LAN. The router is optional, it depends on your connectivity to the WAN. For example, if your ISP offers cable then you probably have a cable modem with an Ethernet connection that you can connect directly to your firewall. When it’s a wireless connection, you probably need the router there for the connection. You will also probably need the router if you do any (advanced) routing like BGP. Most firewalls support some basic routing options: static routes, default routes and sometimes routing protocols like RIP, OSPF or EIGRP.
Stateful Filtering
Firewalls, like routers can use access-lists to check for the source and/or destination address or port numbers. Most routers however, don’t spend much time at filtering…when they receive a packet, they check if it matches an entry in the access-list and if so, they permit or drop the packet. That’s it.
No matter if they receive a single packet or thousands, each packet is treated individually and we don’t keep track of packets we have seen before or not. This is called stateless filtering.
Firewalls, on the other hand, use stateful filtering. They keep track of all incoming and outgoing connections. Here are some examples:
- A computer on the LAN uses its email client to connect to a mail server on the Internet. The client will start the connection with a TCP three-way handshake, which the firewall sees. The firewall will keep track of this connection and when the mail server responds, the firewall will automatically permit this traffic to return to the client.
- A web server is sitting behind a firewall, it’s a busy server that accepts an average of 20 new TCP connections per second from different IP addresses. The firewall keeps track of all connections, once it sees a source IP address that is requesting more than 10 new TCP connections per second, it will drop all traffic from this source IP address, preventing a DoS (Denial of Service).
Packet Inspection
Most firewalls support some form of (deep) packet inspection. Simple access-lists only check source/destination addresses and ports, that’s layer 3 and 4 of the OSI model. Packet inspection means we can inspect up to layer 7 of the OSI model. This means we can look at application data and even the payload:
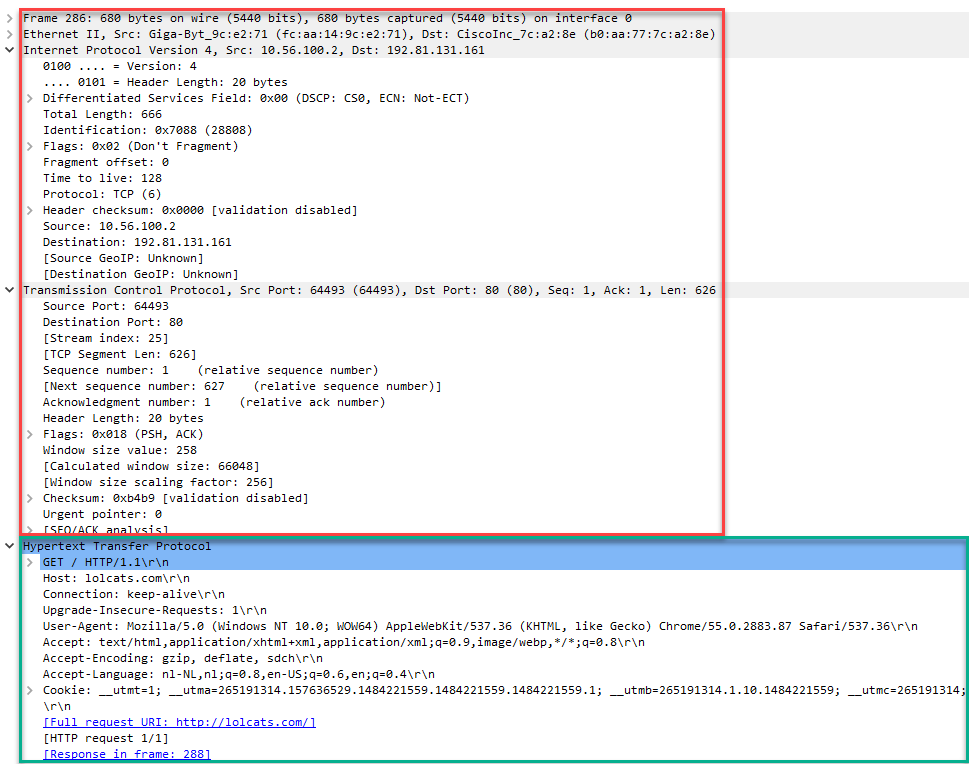
Above you see the network (IP) and transport layer (TCP) marked in red, the application layer is marked with green. This is an example of a webbrowser that is requesting a webpage.
Here are some examples:
- Instead of blocking all IP addresses that belong to lolcats.com, you can create a filter that looks for the URI in HTTP requests and block those instead. You won’t have to worry about IP addresses of web servers that might change in the future.
- Your firewall can check the payload to block any packets that contains known worms or viruses.
Security Zones
Cisco routers, by default, will permit and forward all packets they receive, if they have a matching route in their routing table. If you want to restrict this, you have to configure some access-lists. This can become an administrative nightmare if you have a lot of interfaces and/or access-list rules. Here’s an example:
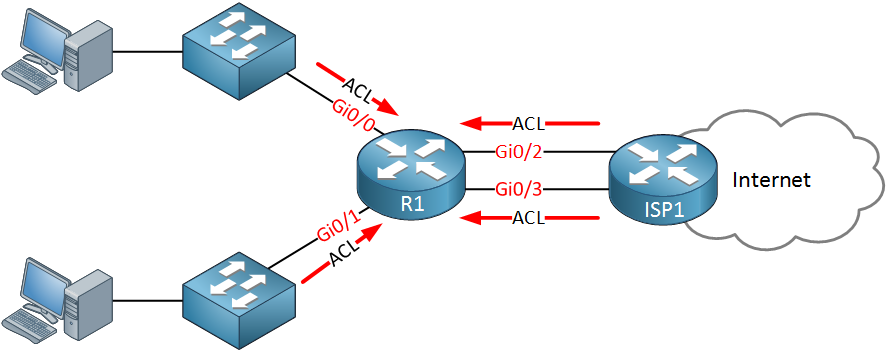
The router above has two incoming access-lists to block some of the traffic from the hosts. We also have two access-lists that prevent traffic from the Internet from entering our network. We might be able to reuse some of the access-lists but we have to apply an access-list to four interfaces.
There is a better solution, firewalls work with security zones. Here’s an example:
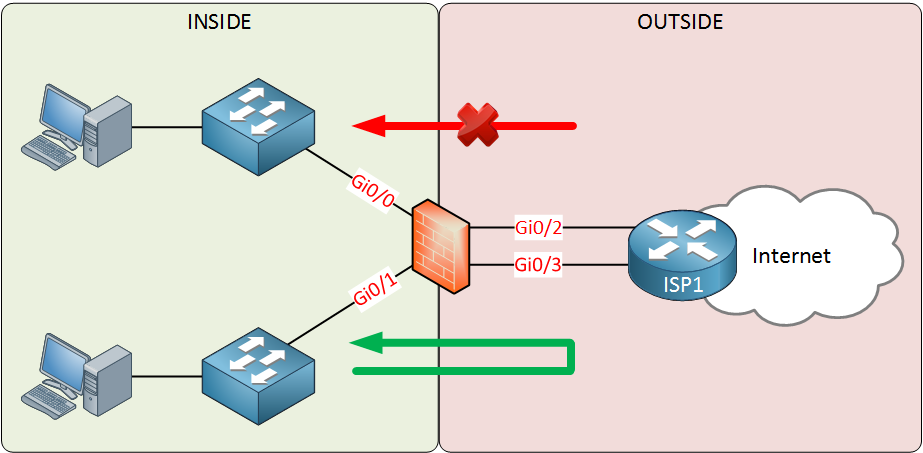
Above we have two security zones:
- INSIDE: this is our LAN
- OUTSIDE: this is our WAN
The interfaces have been assigned to the correct security zone. These zones have two simple rules:
- Traffic from a “high” security level to a “lower” security level is permitted.
- Traffic from a “low” security level to a “higher” security level is denied.
Our LAN is our trusted network, which would have a high security level. The WAN is untrusted so it will have a low security level. This means that traffic from our LAN > WAN will be permitted. Traffic from the WAN to our LAN will be denied. Since the firewall is stateful, it keeps track of outgoing connections and will permit the return traffic from our LAN.
If you want to make an exception, and permit traffic from the WAN to the LAN then this can be accomplished with an access-list.
Most companies will have one or more servers that should be reachable from the Internet. Perhaps a mail or web server. Instead of placing these on the INSIDE, we use a third zone called the DMZ (Demilitarized Zone). Take a look at the picture below:
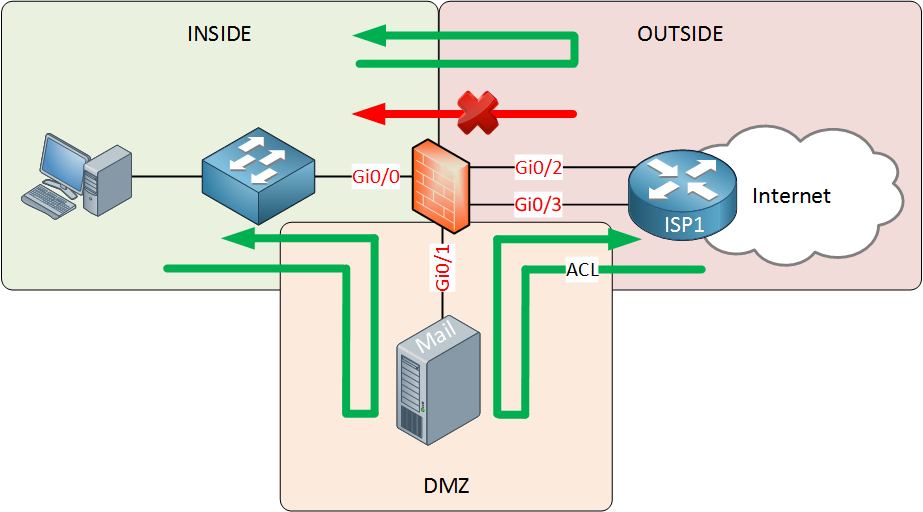
The DMZ security zone will have a security level that is in between the INSIDE and OUTSIDE. This means that:
- Traffic from INSIDE to OUTSIDE is permitted.
- Traffic from INSIDE to DMZ is permitted.
- Traffic from DMZ to OUTSIDE is permitted.
- Traffic from DMZ to INSIDE is denied.
- Traffic from OUTSIDE to DMZ is denied.
- Traffic from OUTSIDE to INSIDE is denied.
To ensure traffic from the OUTSIDE is able to reach the servers in the DMZ, we will use an access-list that only permits traffic to the IP address (and port numbers) that the servers in the DMZ use. This setup is very secure, if one of your servers in the DMZ gets hacked, your INSIDE network will still be secure.
Conclusion
You have now learned the basics of firewalls. Firewalls use stateful filtering to keep track of all incoming and outgoing connections. They are also able (depending on the firewall) to inspect up to layer 7 of the OSI model, looking into the payload of applications.
They also use security zones where traffic from a high security level is permitted to go to a lower security level. Traffic from a low security level to a higher security level will be denied, exceptions can be made with access-lists.

Thanks Rene for your introduction to firewall.
just a friendly feedback, I like a lot your videos when you use the White Board in person with your colored pens, It’s amazing, please keep using it. I feel like I am sitting in a real classroom.
Hi @wisamani,
Glad to hear you like it. I am also trying some “whiteboard” videos on my surface pro like the one in the SDN article:
https://networklessons.com/cisco/ccna-routing-switching-icnd2-200-105/introduction-to-sdn-software-defined-networking/
Do you think those are just as good or still prefer the real whiteboard videos?
Rene
Thanks Rene for your reply, this video is very good, but honestly I am seeing your videos on the white board is much better. They are very strong, very clear and easy to understand.
Thanks for your amazing classes Rene. I just passed CCNP switch.
Thanks for your input Wisam, and grats for passing the SWITCH exam!
Hi @Satish,
Thanks for your feedback. I also prefer the desktop recording, it’s more convenient than a whiteboard that requires cleaning and it’s easier to record from my desk
Laz wrote about the differences between “regular” firewalls and NGFWs awhile ago:
... Continue reading in our forum