Lesson Contents
Management Plane Protection (MPP) is a security feature for Cisco IOS routers that accomplishes two things:
- Restrict the interfaces where the router permits packets from network management protocols.
- Restrict the network management protocols that the router permits.
The management plane is the logical path of all traffic related to the management of the router. For example:
- Telnet
- SSH
- SNMP
- HTTP
- HTTPS
MPP makes it easier to protect management traffic. You need fewer access-lists because you can restrict most of the network management traffic with MPP. It also prevents network management packet flood attacks since it drops denied packets and does not forward them to the CPU. It’s a good tool to permit/deny most of your network management traffic. You can still use access-lists if you need to permit/deny specific subnets and/or IP addresses.
Configuration
Let me show you how to configure MPP. This is the topology we’ll use:
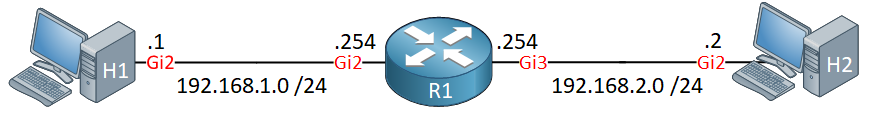
H1 is on a trusted network we use to manage R1. H2 is on a remote network that should not be able to manage R1 with any network management protocols.
Configurations
Want to look for yourself? Here you will find the startup configuration of each device.
H1
hostname H1
!
interface GigabitEthernet2
ip address 192.168.1.1 255.255.255.0
!
endH2
hostname H2
!
interface GigabitEthernet2
ip address 192.168.2.2 255.255.255.0
!
endR1
hostname R1
!
interface GigabitEthernet2
ip address 192.168.1.254 255.255.255.0
!
interface GigabitEthernet3
ip address 192.168.2.254 255.255.255.0
!
endLet’s do a “before” and “after” scenario where you can see the difference between when we use MPP or not.
Without MPP
Let me show you what happens behind the scenes when MPP is disabled. I’ll configure R1 so it only accepts SSH traffic on the VTY lines:
R1(config)#line vty 0 4
R1(config-line)#transport input sshTo see what is going on, we enable a debug:
R1#debug ip packet
IP packet debugging is onLet’s try to telnet from H2 to R1:
H2#telnet 192.168.2.254
Trying 192.168.2.254 ...
% Connection refused by remote hostWe see that the connection is refused, this is expected because we don’t accept telnet on the VTY lines of R1. When you look at R1 you see it sends two packets to H2:
R1#
IP: tableid=0, s=192.168.2.254 (local), d=192.168.2.2 (GigabitEthernet3), routed via FIB
IP: s=192.168.2.254 (local), d=192.168.2.2 (GigabitEthernet3), len 40, sendingR1 responds to H2, refusing the connection. Transmit enough telnet packets from H2 and you can perform a denial of service attack on R1.
With MPP
Let’s see if we can improve this situation. First, let’s enable telnet on the VTY lines of R1:



The control-plane command is not recognized on
3560CX iOS version 15.2
nor on a
3850 IOS-XE version 16.6.6
Is there an alternative?
Hello Bradley
According to this Cisco Documentation, the Cisco IOS Release 15M&T supports these features.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/qos_plcshp/configuration/15-mt/qos-plcshp-15-mt-book/qos-plcshp-cpp.pdf
Now for your specific IOS version, you can take a look at Cisco’s Feature Navigator to see which versions support which features.
I hope this has been helpful!
Laz
Hello Christopher
Remember that Management Plane Protection (MPP) is a subset of Control Plane Policing (CoPP). CoPP is something that is available on all Cisco devices including IOS and NX-OS devices.
Information about CoPP for NX-OS devices can be found here:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/6-x/security/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_Security_Configuration_Guide/b_Cisco_Nexus_9000_Series_NX-OS_Security_Configuration_Guide_chapter_010001.html
Notice the “management plane” section of the document.
Inf
... Continue reading in our forumcool, but even using MPP, I still need ACL to block by IP(Line VTY)
Hello Marlon
The specific example shows how to limit management connectivity to your device via only the interfaces you choose. If you want to further limit connectivity to specific hosts with particular IP addresses, then yes, you must add an access list specifying those addresses. You can do that by referencing an access list using the
access-classcommand under theline vtyconfiguration mode. More information on this can be found here:https://networklessons.com/cisco/ccna-200-301/cisco-ios-telnet-server-client#Security
I hope this has been helpful!
Laz