Let’s configure some access lists so I can demonstrate to you how this is done on Cisco IOS routers. In this lesson, we’ll cover the standard access-list. Here’s the topology:
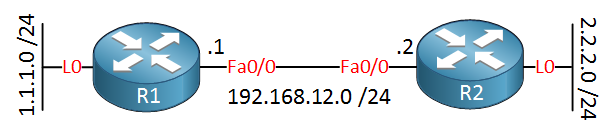
Two routers, and each router has a loopback interface. I will use two static routes so that the routers can reach each other’s loopback interface:
R1(config)#ip route 2.2.2.0 255.255.255.0 192.168.12.2R2(config)#ip route 1.1.1.0 255.255.255.0 192.168.12.1Now let’s start with a standard access-list! I’ll create something on R2 that only permits traffic from network 192.168.12.0 /24:
R2(config)#access-list 1 permit 192.168.12.0 0.0.0.255This single permit entry will be enough. At the bottom of the access-list is a “deny any”. We don’t see it, but it’s there. Let’s apply this access-list inbound on R2:
R2(config)#interface fastEthernet 0/0
R2(config-if)#ip access-group 1 inUse the ip access-group command to apply it to an interface. I applied it inbound with the in keyword.
R2#show ip interface fastEthernet 0/0
FastEthernet0/0 is up, line protocol is up
Internet address is 192.168.12.2/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 1You can verify that the access-list has been applied with the show ip interface command. Above, you see that access-list 1 has been applied inbound.
Now let’s generate some traffic…
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 msOur ping is successful; let’s check the access-list:
R2#show access-lists
Standard IP access list 1
10 permit 192.168.12.0, wildcard bits 0.0.0.255 (27 matches)As you can see, the access-list shows the number of matches per statement. We can use this to verify our access-list. Let me show you something useful when you are playing with access lists:
R1#ping 192.168.12.2 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
U.U.U
Success rate is 0 percent (0/5)When you send a ping you can use the source keyword to select the interface. The source IP address of this IP packet is now 1.1.1.1 and you can see these pings are failing because the access-list drops them.
R2#show access-lists
Standard IP access list 1
10 permit 192.168.12.0, wildcard bits 0.0.0.255 (27 matches)You won’t see them with the show access-list command because the “deny any” is dropping them.
What if I wanted something different? Let’s say I want to deny traffic from network 192.168.12.0 /24 but permit all other networks. I can do something like this:



Good work. I have a question.
I am using Packet Tracer 6.0.1.
I have a network with 2 routers, and 2 PC’s, one on each router. They are on three different networks. 15.x.x.x, 17.x.x.x, and 20.x.x.x. PC1 is on the 15.x.x.x network, and PC2 is on the 17.x.x.x network. They can ping each other before I put in the access-list. (I’m using RIP.)
Then I put in the access list on Router 2
When I ping PC2 from PC1 I get "Reply from 20.1.1.2: Destination ho
... Continue reading in our forumHello George,
The problem is that your ping will make it from pc2 to pc1 will make it, but the return traffic is dropped by your deny entry.
Rene
Hi Rene, I am a nornmally a windows network admin, and have been appointed to put security on our routers and swiches. I know this is a stupid question but when doing access-lists permit, Do I just put the serial address or the eithernet or both? We are running point to point and the router I am working on is remote, so I was going to put the serial address from the our core router to the remote.
I only need the remote side to see our core router so would the command be access-lists 1 permit?
Hi Don,
With the standard access-list you can only create permit or deny statements that match source addresses. If you want a more precise statement you’ll need an extended access-list because it can match on source and destination addresses.
Rene
Rene,
You mentioned “ill show you how to modify the access-list without deleting the whole thing” but I didnt find it in this lesson. Can you please explain ?