Lesson Contents
IPv6 DHCPv6 Guard is one of the IPv6 FHS (First Hop Security) mechanisms and is very similar to IPv4 DHCP snooping.
This feature inspects DHCPv6 messages between a DHCPv6 server and DHCPv6 client (or relay agent) and blocks DHCPv6 reply and advertisements from (rogue) DHCPv6 servers. DHCPv6 messages from clients or relay agents to a DHCPv6 server are not affected.
In this lesson, I’ll show you how to configure IPv6 DHCPv6 guard.
Configuration
Here is the topology we’ll use:
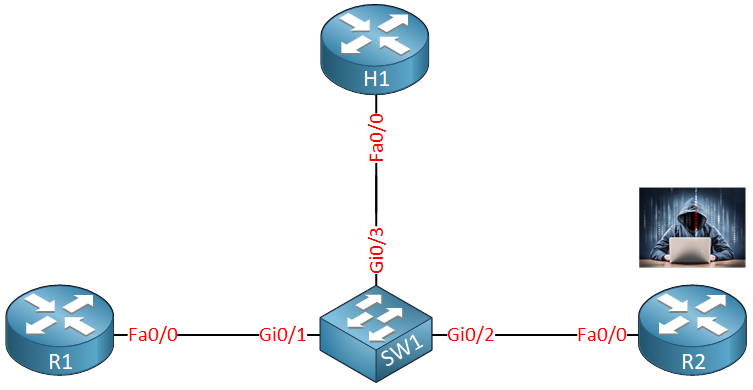
We have four devices:
- R1 is our legitimate DHCPv6 server.
- R2 is a rogue DHCPv6 server.
- H1 is a DHCPv6 client.
- SW1 is where we configure IPv6 DHCPv6 guard.
Basic Policy
We’ll start with a simple example where we configure R1 as a DHCPv6 server and block the rogue DHCPv6 server with a DHCPv6 guard policy.
Let’s configure R1 as a DHCPv6 server:
R1(config)#ipv6 unicast-routing
R1(config)#ipv6 dhcp pool MY_POOL
R1(config-dhcpv6)#address prefix 2001:DB8:0:1::/64
R1(config)#interface FastEthernet 0/0
R1(config-if)#ipv6 enable
R1(config-if)#ipv6 dhcp server MY_POOLR1 is a simple DHCPv6 server, I only advertise a prefix and that’s it. Let’s configure H1 as a DHCPv6 client:
H1(config)#interface FastEthernet 0/0
H1(config-if)#ipv6 enable
H1(config-if)#ipv6 address dhcpLet’s see if H1 gets an IPv6 address:
R1#show ipv6 dhcp binding
Client: FE80::217:5AFF:FEED:7AF0
DUID: 0003000100175AED7AF0
Username : unassigned
IA NA: IA ID 0x00030001, T1 43200, T2 69120
Address: 2001:DB8:0:1:ED29:C746:E04B:5784
preferred lifetime 86400, valid lifetime 172800
expires at Apr 27 2018 01:47 PM (172704 seconds)H1#show ipv6 interface brief | include 2001
2001:DB8:0:1:ED29:C746:E04B:5784Excellent. Let’s configure a DHCPv6 guard policy so that this setup is protected. I need to create two policies, one for the DHCPv6 server, another one for the DHCPv6 client:
SW1(config)#ipv6 dhcp guard policy DHCP_SERVER
SW1(config-dhcp-guard)#device-role serverSW1(config)#ipv6 dhcp guard policy DHCP_CLIENT
SW1(config-dhcp-guard)#device-role clientRight now, my policies are empty and I only set the device role. Client is the default role so you don’t have to configure it. For the sake of completeness, I did it anyway.
Let’s attach the DHCP_SERVER policy to the interface that connects to R1 and the DHCP_CLIENT policy to the correct interfaces:
SW1(config)#interface GigabitEthernet 0/1
SW1(config-if)#ipv6 dhcp guard attach-policy DHCP_SERVER
SW1(config)#interface range GigabitEthernet 0/2 - 3
SW1(config-if-range)#ipv6 dhcp guard attach-policy DHCP_CLIENTWe can verify our configuration with the following command:
SW1#show ipv6 dhcp guard policy
Dhcp guard policy: DHCP_CLIENT
Device Role: dhcp client
Target: Gi0/2 Gi0/3
Dhcp guard policy: DHCP_SERVER
Device Role: dhcp server
Target: Gi0/1
Max Preference: 255
Min Preference: 0This gives a nice overview of the policies and to which interfaces we attached them. Let’s see if it works though…
To test this, I’ll shut the interface of R1:
R1(config)#interface FastEthernet 0/0
R1(config-if)#shutdownAnd we’ll configure a DHCPv6 server on our rogue DHCPv6 server:
R2(config)#ipv6 unicast-routing
R2(config)#ipv6 dhcp pool ROGUE_POOL
R2(config-dhcpv6)#address prefix 2001:DB8:BAD:C0DE::/64
R2(config)#interface FastEthernet 0/0
R2(config-if)#ipv6 enable
R2(config-if)#ipv6 dhcp server ROGUE_POOLBefore we request another IPv6 address on the host, let’s enable a debug on SW1 so that we can see everything in action:
SW1#debug ipv6 snooping dhcp-guard
IPv6 snooping - DHCP Guard debugging is onNow reset the DHCPv6 client:
H1#clear ipv6 dhcp client FastEthernet 0/0This is what you’ll see on the switch:
SW1#
SISF[DHG]: Gi0/3 vlan 1 DHCP Client message for role dhcp client - Permit
SISF[DHG]: Gi0/2 vlan 1 DHCP Server message for role dhcp client - Deny
In the output above, you can see that the DHCPv6 client messages are permitted but the DHCPv6 server messages are dropped because we shouldn’t receive those on a “client” interface.
Prefix Filtering
Anything else we can do? First, let’s get rid of the rogue DHCPv6 server and enable the legitimate DHCPv6 server:
H2(config)#interface FastEthernet 0/0
H2(config-if)#shutdownR1(config)#interface FastEthernet 0/0
R1(config-if)#no shutdownLet’s take a closer look at the DHCP_SERVER policy we created:



Hi Rene,
Does the DHCPv6 GUARD feature also builds a binding table to be used with IPV6 Source Guard?
Thanks in advanced.
Hello Nitay
The binding table is built by the DHCPv6 feature itself. The DHCPv6 Guard feature prevents the binding table from registering DHCPv6 replies and advertisements from rogue DHCPv6 servers. So DHCPv6 Guard protects the binding table from being populated by an non-endorsed source.
This protected binding table is then used by IPv6 Source Guard to filter inbound traffic on L2 switch ports that are not in the IPv6 binding table. More info on the IPv6 Source Guard feature can be found at the following link.
https://networklessons.com/cisco/ccie-routing-sw
... Continue reading in our forumHi Laz,
Thanks for your reply.
Does the DHCPv6 Feature is an built-in Feature on every IPv6 capable switch,and the DHCPv6 Feature works just like dhcpv4 snooping when configured statically on a switch with the command
ip dhcp snooping?Thanks again very much, I appreciate your time!
Hello Nitay
DHCP Snooping uses a little bit of a different philosophy compared to IPv6 DHCPv6 Guard. Where DHCP snooping configures trusted and untrusted ports, IPv6 DHCP Guard is capable of creating client or server policies per port, is able to filter based on specific prefixes, and can also take advantage of preference filtering as stated in the lesson. IPv6 DHCP Guard does not create a table that is similar to the DHCP snooping table.
I hope this has been helpful!
Laz
Thanks Laz,
You mentioned the “DHCPv6 Feature” as a whole different feature compared to the “DHCPv6 Guard Feature”, and you mentioned that the first one is building the binding table.
I understand that the DHCPv6 Guard is used exactly like port-security which you must configure it on each and every port that should be connected to an end device, otherwise an attacker could spoof DHCPv6 messages.
I also learned that you have IPV6 snooping Feature in the IPv6 Source Guard Lesson but again - you mentioned that “DHCPv6 Feature” and now I wonder if you meant DHCPv6
... Continue reading in our forum