Lesson Contents
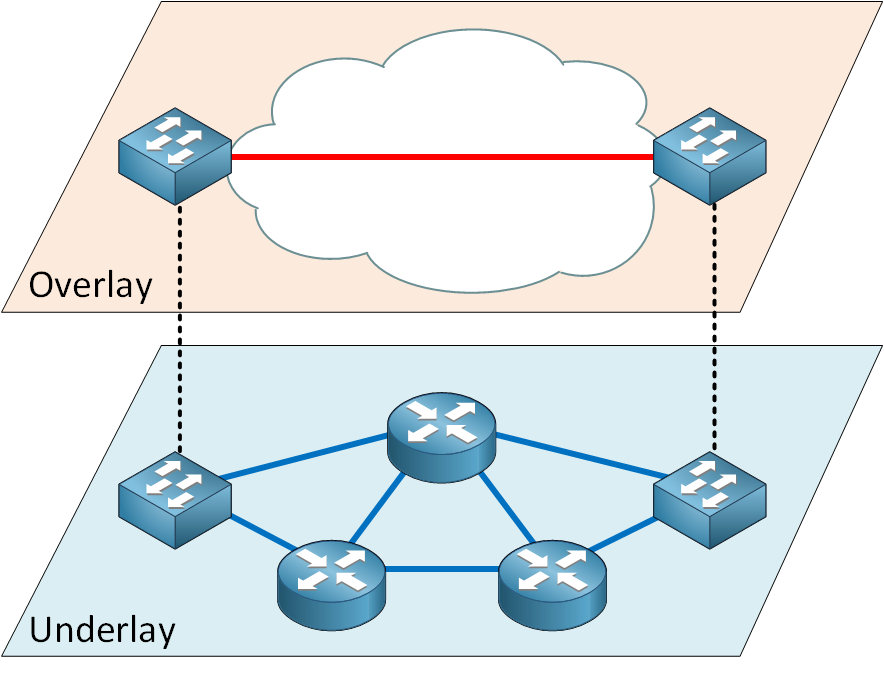
With overlay networking, we create an overlay network, which is a virtual network on top of the underlay network, which is the physical network. We use encapsulation to wrap the original data packet or frame in a new packet or frame with an overlay header. The job of the underlay network is to get packets or frames from A to B. It is a simple network whose main job is transportation.
The complexity is in the overlay network(s). This is where we implement our network segmentation, routing logic, security rules, Quality of Service (QoS) policies, and more.
Before we dive into the details, it’s helpful to understand the problem that overlay networking solves. A traditional network, built only on physical hardware (an underlay network), has limitations:
- Forwarding limitations: Data forwarding is tied to physical paths. If you want traffic engineering, you need to reconfigure the physical network, such as changing IGP metrics, policy-based routing, or even re-cabling.
- Slow deployments: If you want to add a new tenant or isolated segment, you need to configure VLANs, ACLs, and routing policies on many devices, which is time-consuming and prone to errors.
- Scalability issues: VLANs have limits (4094 usable VLANs), which is not enough for large-scale cloud providers or data centers.
Nowadays, overlay networking is associated with modern technologies and protocols like Virtual Extensible LAN (VXLAN) and Software Defined Networking (SDN). However, the concept has been around for decades. For example, with VPNs, we create secure tunnels over the public Internet, and even the original Internet, which ran over the telephone network (PSTN), can be seen as a type of overlay network.
Modern datacenters use overlay networks. It’s also used in fabrics like Cisco ACI and VMware NSX because they allow massive scale and automation. Enterprise networks use overlay networks with SD-WAN and products like Cisco SD-Access. Cloud provider networks are built on large multi-tenant overlay networks. This is how they create isolated logical networks for millions of customers on shared hardware.
In this lesson, we’ll take a look at what overlay networking is about, its advantages, disadvantages, and some example technologies. Let’s get started.
Underlay Network
Let’s take a closer look at the underlay network. This is the physical network infrastructure, which includes our routers, switches, and the physical media that connects them, such as fiber optic or copper cabling.
The primary role of the underlay network is to provide simple, reliable connectivity between all tunnel endpoints. These are the devices that perform the encapsulation and decapsulation for the overlay network. Routers, switches, and hypervisors are all examples of devices that can be tunnel endpoints. Depending on the technology, they are called tunnel endpoints, overlay endpoints, tunnel edges, or more specific names such as VXLAN Tunnel Endpoint (VTEP). The underlay network doesn’t need to know about anything that happens within the overlay network(s), such as customer routes or policies. Its only purpose is to be a transport network for the overlay network. The underlay network should provide full connectivity, high bandwidth, low latency, and high availability. This means you’ll see technologies like:
- Equal-Cost Multi-Path (ECMP) for redundant paths and load sharing
- Fast convergence mechanisms to handle failures instantly:
- Bidirectional Forwarding Detection (BFD) for rapid failure detection
- Fast Reroute (FRR) mechanisms like Loop-Free Alternate (LFA) to pre-calculate backup paths.
The underlay network also requires an increased MTU because of encapsulation overhead. QoS is important to prioritize traffic based on the outer (underlay) or inner (overlay) packet headers.
Nowadays, the underlay network is typically a Layer 3 routed fabric with routing protocols such as OSPF, IS-IS, or BGP.
Overlay Network
The overlay network is the virtual (logical) network that is built on top of the underlay network. This is usually done using tunneling. Overlay networks can provide Layer 2 (bridging) or Layer 3 (routing) services over the underlay network.
To separate different overlay networks and traffic from different tenants, we use unique identifiers. This depends on the technology we use, but this could be as simple as a VLAN ID. Other examples are a VXLAN VNI, MPLS label, or VRF ID.
Encapsulation and decapsulation are done on the data plane, but overlay networks also require a control plane to exchange routes, policies, and more. Its job is to distribute the necessary information to the tunnel endpoints so they can forward traffic correctly. This includes:
- Endpoint Discovery: Learning the underlay address of other tunnel endpoints.
- Address Advertisement: Distributing Layer 2 MAC addresses and/or Layer 3 IP prefixes that exist within the overlay network.
- Policy Distribution: Pushing security policies, QoS markings, or traffic engineering decisions to the endpoints.
Depending on the technology you use, this can be as simple as flood and learn data plane learning, similar to how traditional Ethernet switches learn MAC addresses. There are more advanced control plane options, though. For example:
- LISP (Locator/ID Separation Protocol), which has an EID-to-RLOC database. This functions much like DNS does for domain names, providing the current location (RLOC) for a given identity (EID).
- VXLAN can use MP-BGP EVPN to advertise route information and policies.
Overlay Networking Technologies
Now that you have a high-level understanding of overlay networking, let’s take a look at some specific technologies. These examples range from basic concepts to the modern protocols that power modern data centers and WANs.
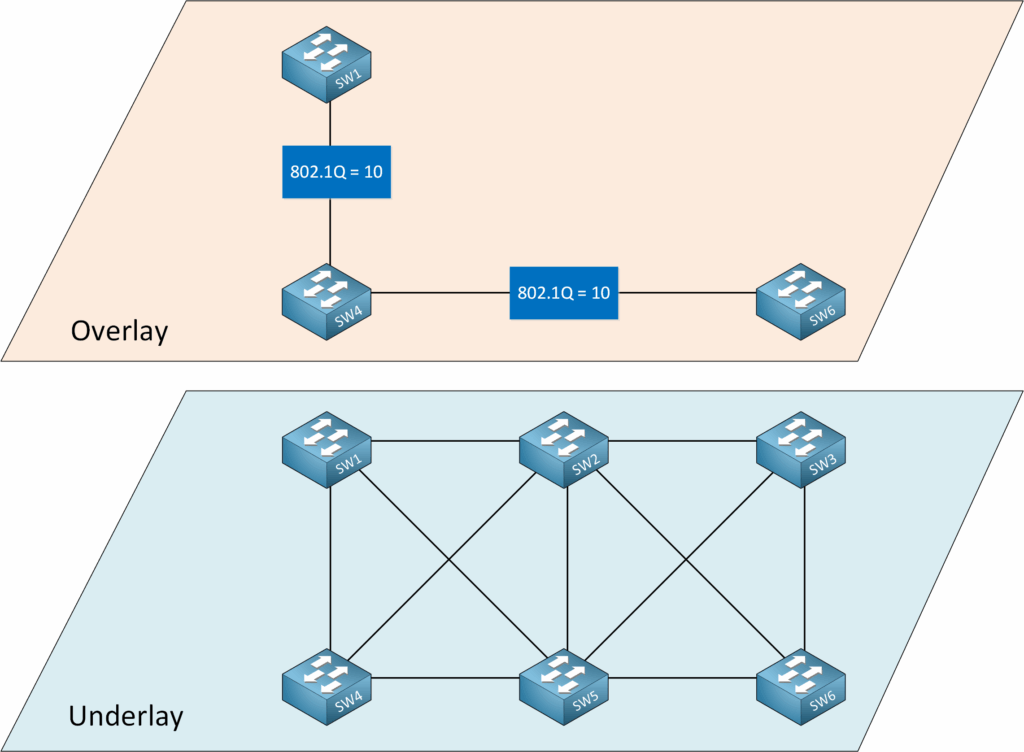
Virtual Local Area Networks (VLANs)
VLANs can be considered one of the earliest and simplest forms of overlay networking. You could say it’s not a real overlay because there is no encapsulation, but still, it illustrates the core concept. We can create multiple logical, isolated networks on a single shared physical infrastructure by adding an 802.1Q header to an Ethernet frame. Each VLAN is a simple Layer 2 overlay network. By using different Spanning Tree (STP) root bridges, we get different traffic paths for each VLAN.
Generic Routing Encapsulation (GRE)
GRE is a tunneling protocol developed by Cisco. You can use it to encapsulate different network layer protocols inside virtual point-to-point links over an IP network. GRE takes an IP or IPv6 packet, adds a GRE header and a new IP header for the underlay network. The result is a standard IP packet that can be routed on the underlay network.
Virtual Private Network (VPN)
When you need to create a secure tunnel over an untrusted underlay like the public Internet, you use a VPN so you can authenticate and encrypt your traffic. For example, IPSec can operate in tunnel mode, where it encrypts the original IP packet and encapsulates it inside a new IP packet with a new header. The IP packet can be transmitted over the public underlay network while the inner IP packet is encrypted. This is often used for secure remote access or site-to-site connections.
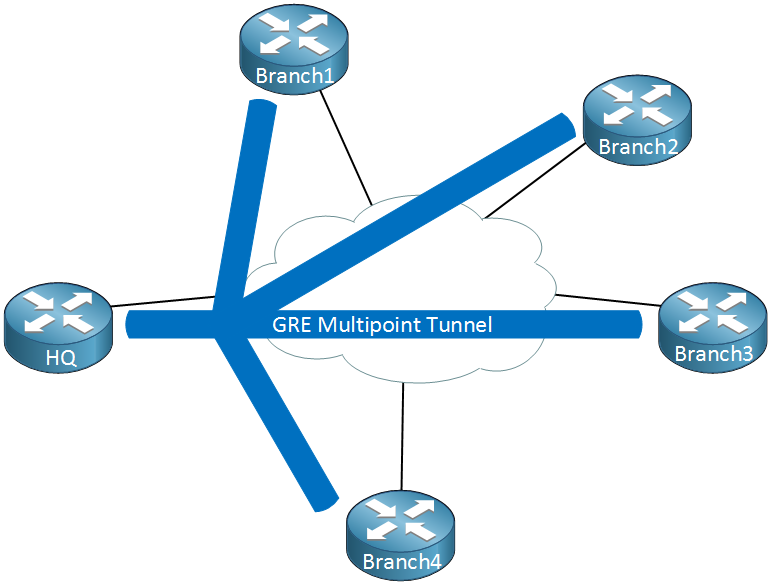
Dynamic Multipoint VPN (DMVPN)
DMVPN is a popular solution for connecting many sites (like branch offices) in a hub-and-spoke or dynamic full-mesh topology without needing to manually configure tunnels between every site. DMVPN combines multiple technologies. It uses GRE for encapsulation (mGRE, or multipoint GRE), IPSec for security, and a control plane protocol called NHRP (Next Hop Resolution Protocol). NHRP allows spokes to dynamically discover the public (underlay) IP address of other spokes to build direct spoke-to-spoke tunnels on demand.
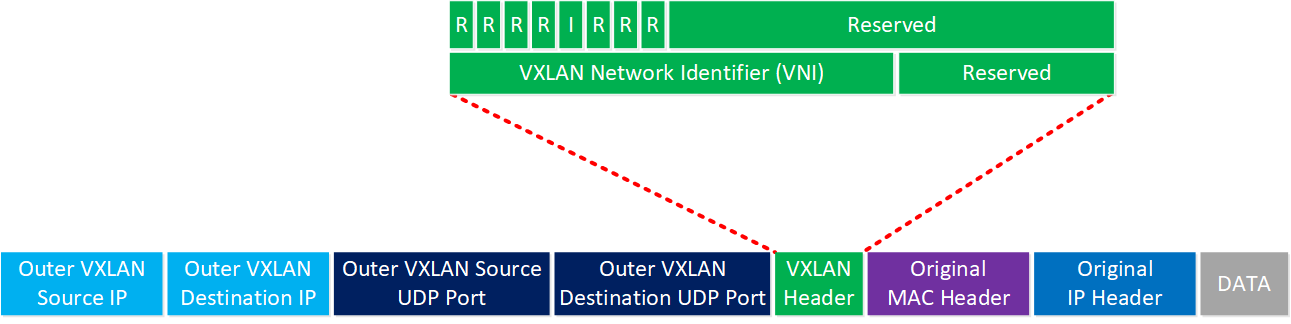
Virtual Extensible LAN (VXLAN)
VXLAN is a popular overlay networking technology in modern data centers. VXLAN extends Layer 2 segments over a Layer 3 underlay network. It encapsulates a complete Layer 2 Ethernet frame into a UDP packet and uses a 24-bit identifier called the VNI (VXLAN Network Identifier), which allows for over 16 million unique segments.
Locator/ID Separation Protocol (LISP)
LISP is a protocol that addresses an Internet architecture problem: IP addresses represent both a device’s identity and its location. LISP splits these two functions. A device is assigned a permanent Endpoint Identifier (EID), and its current location in the network topology is represented by a Routing Locator (RLOC). A distributed mapping system, similar to DNS, is used to look up the current RLOC for an EID. This allows an EID (and the device it represents) to move from one location (RLOC) to another without its IP address having to change.
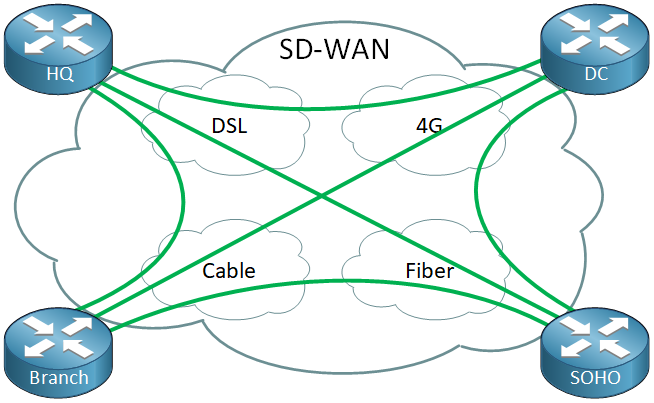
Software-Defined Wide Area Network (SD-WAN)
SD-WAN leverages overlay networking for WANs. It abstracts the underlying transport network(s) and provides centralized control and application-aware routing. SD-WAN solutions deploy overlay tunnels (typically IPSec) over any available underlay transport, such as MPLS, broadband Internet, and LTE. A centralized controller manages policies and monitors the real-time performance of these underlay links. Traffic is then intelligently transmitted across the best available path based on the application’s requirements. For example, sending voice traffic over the lowest-latency link and bulk data over the highest-bandwidth link.
Advantages
Overlay networking has become a popular choice in modern networks because it offers quite a few advantages. Let’s look at the most important ones.
Decoupling
The overlay and underlay networks are managed as two separate networks. The underlay network focuses on one single job: providing simple, stable, and highly available IP reachability between physical endpoints. The overlay network focuses on delivering services like tenant segmentation, security policies, and custom routing without ever touching the physical hardware. This separation of concerns simplifies operations.
Agility
Because overlay networks are software-defined, they are agile. It’s easy to deploy a new isolated network for a customer or application. You don’t have to configure VLANs, ACLs, routing, etc., on multiple devices. With a centralized controller and APIs, it’s easy to configure a new overlay network in a short time. This aligns with modern DevOps and “Infrastructure as Code” (IaC) workflows.
Scalability
Traditional networking protocols were not designed for the scale of modern cloud and data center networks. The limit of 4094 VLANs is not enough for modern networks. Overlay technologies such as VXLAN, with its 24-bit VNI, support over 16 million unique segments on the same physical infrastructure.
Disadvantages
Although overlay networking offers many advantages, but there are some disadvantages as well. Let’s take a look.
Complexity
Instead of a single network, you now have two networks to worry about. The underlay and overlay networks. Each has its own state, control plane, and failure domains. An issue in the overlay network could be caused by an issue in the underlay network or vice versa.
Overhead
Encapsulation and decapsulation are not free processes. They consume compute resources on the tunnel endpoints. If the tunnel endpoint is a virtual machine, virtual router, or hypervisor, then the CPU has to do encapsulation and decapsulation, which might limit throughput and increase latency. With hardware-based tunnel endpoints like switches, encapsulation and decapsulation are offloaded to ASICs, but that means that your hardware has to support the overlay protocol. If not, performance will be an issue.
Another issue is that every packet or frame sent across the overlay network must be encapsulated and contain additional headers (e.g., VXLAN, GRE, IPSec). These extra headers consume bandwidth. For a VXLAN packet, this can be 50 bytes or more, meaning for every packet, you are using more of your link’s capacity on overhead rather than payload. Modern networks usually use jumbo frames (MTU of 9000 bytes or higher), which is why this is less of an issue.
Troubleshooting
Troubleshooting overlays can be more difficult than traditional networks. A traceroute from a host inside an overlay only shows the logical path. It won’t show the physical underlay network path that the encapsulated packets are taking. To diagnose a problem, you might need tools that help you understand what the logical and physical path is. Otherwise, the underlay network is a black box.
Comparison
We covered the most important items to understand overlay networking. Let me give you an overview that shows the main differences between the underlay and overlay networks:
| Feature | Underlay Network | Overlay Network |
|---|---|---|
| Definition | Physical network infrastructure | Virtual network built on top of the underlay network |
| Primary Purpose | Provide simple, reliable connectivity between tunnel endpoints | Implement network segmentation, routing logic, security rules, and QoS policies |
| Implementation | Hardware-based (physical routers, switches, cables) | Software-defined using encapsulation and tunneling protocols |
| Scalability | Limited by physical constraints and protocols | Massive scalability (For example: VXLAN supports 16+ million segments) |
| Deployment Speed | Slow: requires manual configuration of VLANs, ACLs, routing policies | Fast: can be provisioned in minutes using centralized controllers and APIs |
| Traffic Engineering | Requires reconfiguring physical network, changing IGP metrics, or re-cabling | Flexible routing and traffic steering through software control |
| Network Layer | Typically Layer 3 routed fabric with OSPF, IS-IS, or BGP | Can provide Layer 2 or Layer 3 services |
| Control Plane | Traditional routing protocols for simple reachability | Advanced control plane for endpoint discovery, address advertisement, and policy distribution |
| Multi-tenancy | Limited support, difficult to implement isolation | Native multi-tenancy with unique identifiers (VNI, VLAN ID, MPLS label) |
| Packet Processing | Standard packet forwarding without encapsulation overhead | Encapsulation/decapsulation adds overhead and requires additional processing |
| Examples | Physical switches, routers, hypervisors, copper, and fiber optic cables | VXLAN, GRE, VPNs, DMVPN, SD-WAN, LISP |
Conclusion
And that’s it. You have now learned the basics of overlay networking: