Lesson Contents
The FlexVPN hub and spoke topology can be useful when you have a central site and multiple remote sites. After configuring the hub and your first spoke router, adding extra spoke routers is easy. This is a scalable solution and because we use IKEv2, everything is encrypted with IPSec. FlexVPN is an improvement over DMVPN and is sometimes (unofficially) referred to as DMVPN phase 4.
FlexVPN uses virtual tunnel interfaces (VTI), an alternative to the older crypto-maps. There are two VTI types:
- Dynamic VTI (DVTI)
- Static VTI (VTI)
In the first FlexVPN IKEv2 smart defaults lesson, we used static VTIs. This is a “regular” tunnel interface.
With dynamic VTI, we use a single virtual template on our hub router. Whenever a new IPSec session is needed, the router automatically creates a virtual access interface that is cloned from the virtual template.
With two remote spoke routers, you will have one virtual-template and two virtual-access interfaces.
The virtual template can include most of what you would use on a regular interface. You can add access-lists, policy-maps for QoS, etc. These are all copied to the virtual access interfaces. The DVTI makes it easy to create lots of IPSec sessions with remote peers.
With the hub and spoke topology, we use a dynamic VTI on the hub and static VTIs on the spoke routers.
Configuration
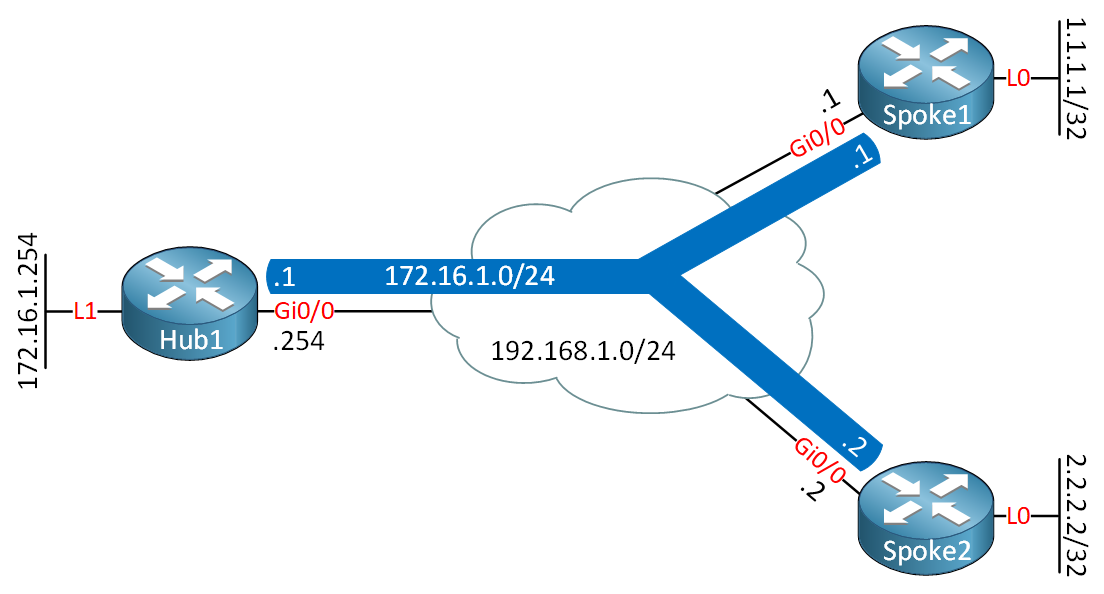
Let’s see how we can configure FlexVPN hub and spoke. This is the topology I am going to use:
The three routers are connected on the 192.168.1.0/24 network using their GigabitEthernet 0/0 interfaces.
- The hub router has a loopback 1 interface with an IP address we will use for the dynamic VTI interface.
- Each spoke router has a loopback 0 interface which simulates a network behind the spoke router.
I used IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.9(3)M2 for this example.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
Hub1
hostname Hub1
!
ip cef
!
interface Loopback1
ip address 172.16.1.254 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.1.254 255.255.255.0
!
endSpoke1
hostname Spoke1
!
ip cef
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.1.1 255.255.255.0
!
endSpoke2
hostname Spoke2
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.1.2 255.255.255.0
!
endHub1
We’ll start with the hub router.
IKEv2 Keyring
For this example, we’ll use pre-shared keys (PSK). You could configure a unique PSK for each spoke but to keep it simple, I’ll use a single PSK for all spoke routers. On a real network, PKI authentication would be a better option. Here is the keyring:
Hub1(config)#crypto ikev2 keyring IKEV2_KEYRING
Hub1(config-ikev2-keyring)#peer SPOKE_ROUTERS
Hub1(config-ikev2-keyring-peer)#address 0.0.0.0 0.0.0.0
Hub1(config-ikev2-keyring-peer)#pre-shared-key local CISCO
Hub1(config-ikev2-keyring-peer)#pre-shared-key remote CISCOIKEv2 Authorization Policy
I’m going to use IKEv2 routing so that the hub advertises a default route to the spoke routers:
Hub1(config)#aaa new-model
Hub1(config)#aaa authorization network FLEXVPN_LOCAL local
Hub1(config)#crypto ikev2 authorization policy IKEV2_AUTHORIZATION
Hub1(config-ikev2-author-policy)#route set interface
Hub1(config-ikev2-author-policy)#route set access-list FLEXVPN_ROUTES
Hub1(config)#ip access-list standard FLEXVPN_ROUTES
Hub1(config-std-nacl)#permit anyIKEv2 Profile
We need an IKEv2 profile that contains the local and remote identity. We could create an entry for each spoke router but instead, I’ll configure the hub router so that it only checks the domain “FLEXVPN.LAB”. This makes it easier to connect spoke routers in the future.
Hub1(config)#crypto ikev2 profile IKEV2_PROFILE
Hub1(config-ikev2-profile)#match identity remote fqdn domain FLEXVPN.LAB
Hub1(config-ikev2-profile)#identity local fqdn HUB.FLEXVPN.LAB
Hub1(config-ikev2-profile)#authentication remote pre-share
Hub1(config-ikev2-profile)#authentication local pre-share
Hub1(config-ikev2-profile)#keyring local IKEV2_KEYRING
Hub1(config-ikev2-profile)#aaa authorization group psk list FLEXVPN_LOCAL IKEV2_AUTHORIZATION
Hub1(config-ikev2-profile)#virtual-template 1IPSec Profile
We need an IPSec profile where we specify the IKEv2 profile:
Hub1(config)#crypto ipsec profile IPSEC_PROFILE
Hub1(ipsec-profile)#set ikev2-profile IKEV2_PROFILEDynamic VTI
Because the hub connects to multiple spoke routers, we need a dynamic VTI. I want to use an IP address in the same subnet as the tunnel interfaces on the spoke routers. However, you can’t configure the IP address directly on the dynamic VTI interface. If you are curious why, what happens is that the router refuses to copy the IP address to virtual-access interfaces it creates. We have to use the ip unnumbered command to “copy” the IP address to the virtual-access interfaces. I assigned the IP address I want to use for the tunnel to the loopback 1 interface. We also attach the IPSec profile to the dynamic VTI interface. Here is the configuration:
Hub1(config)#interface Virtual-Template 1 type tunnel
Hub1(config-if)#ip unnumbered loopback 1
Hub1(config-if)#tunnel protection ipsec profile IPSEC_PROFILEThis completes the configuration of the hub router.
Spoke1
Now it’s time for our first spoke router.
IKEv2 Keyring
Let’s start with that keyring. This is where I specify the hub and the PSKs:
Spoke1(config)#crypto ikev2 keyring IKEV2_KEYRING
Spoke1(config-ikev2-keyring)#peer HUB1
Spoke1(config-ikev2-keyring-peer)#address 192.168.1.254
Spoke1(config-ikev2-keyring-peer)#pre-shared-key local CISCO
Spoke1(config-ikev2-keyring-peer)#pre-shared-key remote CISCOIKEv2 Authorization Policy
We need an IKEv2 authorization policy because I want to advertise the network on the loopback0 interface to the hub router. Here’s what it looks like:
Spoke1(config)#aaa new-model
Spoke1(config)#aaa authorization network FLEXVPN_LOCAL local
Spoke1(config)#crypto ikev2 authorization policy IKEV2_AUTHORIZATION
Spoke1(config-ikev2-author-policy)#route set interface
Spoke1(config-ikev2-author-policy)#route set access-list FLEXVPN_ROUTES
Spoke1(config)#ip access-list standard FLEXVPN_ROUTES
Spoke1(config-std-nacl)#permit host 1.1.1.1IKEv2 Profile
In the IKEv2 profile, we configure the identity of the remote hub router and local identity (SPOKE1.FLEXVPN.LAB). We configured the hub router so it only checks the domain part (FLEXVPN.LAB).
Spoke1(config)#crypto ikev2 profile IKEV2_PROFILE
Spoke1(config-ikev2-profile)#match identity remote fqdn HUB.FLEXVPN.LAB
Spoke1(config-ikev2-profile)#identity local fqdn SPOKE1.FLEXVPN.LAB
Spoke1(config-ikev2-profile)#authentication local pre-share
Spoke1(config-ikev2-profile)#authentication remote pre-share
Spoke1(config-ikev2-profile)#keyring local IKEV2_KEYRINGIPSec Profile
Let’s create an IPSec profile and specify the IKEv2 profile we want to use:
Spoke1(config)#crypto ipsec profile IPSEC_PROFILE
Spoke1(ipsec-profile)#set ikev2-profile IKEV2_PROFILEStatic VTI
On the spoke routers, we use a “regular” static VTI (tunnel interface):
Spoke1(config)#interface Tunnel 0
Spoke1(config-if)#ip address 172.16.1.1 255.255.255.0
Spoke1(config-if)#tunnel source GigabitEthernet 0/0
Spoke1(config-if)#tunnel destination 192.168.1.254
Spoke1(config-if)#tunnel protection ipsec profile IPSEC_PROFILEThis completes the configuration of the first spoke router.
Spoke2
We’ll configure the exact same thing (except for the IP addresses and local identity) on the second spoke router:
Spoke2(config-ikev2-author-policy)#crypto ikev2 keyring IKEV2_KEYRING
Spoke2(config-ikev2-keyring)#peer HUB1
Spoke2(config-ikev2-keyring-peer)#address 192.168.1.254
Spoke2(config-ikev2-keyring-peer)#pre-shared-key local CISCO
Spoke2(config-ikev2-keyring-peer)#pre-shared-key remote CISCO
Spoke2(config)#aaa new-model
Spoke2(config)#aaa authorization network FLEXVPN_LOCAL local
Spoke2(config)#crypto ikev2 authorization policy IKEV2_AUTHORIZATION
Spoke2(config-ikev2-author-policy)# route set interface
Spoke2(config-ikev2-author-policy)# route set access-list FLEXVPN_ROUTES
Spoke2(config-if)#ip access-list standard FLEXVPN_ROUTES
Spoke2(config-std-nacl)# permit 2.2.2.2
Spoke2(config-ikev2-keyring-peer)#crypto ikev2 profile IKEV2_PROFILE
Spoke2(config-ikev2-profile)#match identity remote fqdn HUB.FLEXVPN.LAB
Spoke2(config-ikev2-profile)#identity local fqdn SPOKE2.FLEXVPN.LAB
Spoke2(config-ikev2-profile)#authentication remote pre-share
Spoke2(config-ikev2-profile)#authentication local pre-share
Spoke2(config-ikev2-profile)#keyring local IKEV2_KEYRING
Spoke2(config-ikev2-profile)#aaa authorization group psk list FLEXVPN_LOCAL default
Spoke2(config-ikev2-profile)#crypto ipsec profile IPSEC_PROFILE
Spoke2(ipsec-profile)#set ikev2-profile IKEV2_PROFILE
Spoke2(ipsec-profile)#interface Tunnel0
Spoke2(config-if)#ip address 172.16.1.2 255.255.255.0
Spoke2(config-if)#tunnel source GigabitEthernet0/0
Spoke2(config-if)#tunnel destination 192.168.1.254
Spoke2(config-if)#tunnel protection ipsec profile IPSEC_PROFILEThis completes our configuration of the hub and spoke routers.
Verification
Let’s verify our work. First, let’s see if there is an IKEv2 security association (SA):
Hub1#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.1.254/500 192.168.1.1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/463 sec
Tunnel-id Local Remote fvrf/ivrf Status
2 192.168.1.254/500 192.168.1.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/461 sec
IPv6 Crypto IKEv2 SAOur hub router has two SAs, one for each spoke router. Let’s check the IPSec SA:



Hi Rene and Team,
How about if I use 1 Router is same ISP, spoke routers will have different IP public, so we need one default route to ISP. So my question is: in the case. can we do Hub advertise 0.0.0.0/0 to spoke routers ? and when I did lab in this case, My lab can not advertise subnet to peer , can you show idea to troubleshoot ?
, can you show idea to troubleshoot ?
Thank a lot !
Hello Tung
You must remember that in such a topology, you have an overlay network and an underlay network. The underlay network in the lesson is the 192.168.1.0/24 network. This represents the Internet or any other network over which you will create your tunnels. This underlay network can be anything, using the same ISPs or different ISPs, just as long as the routers have connectivity between them. The routing between routers here is the responsibility of the ISPs. In fact, a static IP is needed only for the hub. The IP addresses of the spokes can actuall
... Continue reading in our forumHello Terry
Yes, you seem to be correct. I will let @Rene know…
Laz
Thanks Terry. I just fixed this.
Rene
Hello Laz ,
how does the Hub Router advertise the default Route to Spoke ? with access list
permit any? BUT There is no command to advetise the default route or this will occur automatically ?Thanks in Advanced .