Lesson Contents
In our FlexVPN site-to-site smart defaults lesson, we configure a site-to-site VPN using smart defaults. In this lesson, we’ll configure the same thing but we are not going to use smart defaults. This means we have to configure all of this:
- IKEv2
- IKEv2 Proposal
- IKEv2 Policy
- IKEv2 Keyring
- IKEv2 Profile
- IPSec
- IPSec Transform-set
- IPSec Profile
I’ll walk you through the entire configuration and we’ll take a look at some show commands to verify our work.
Configuration
This is the topology we are going to use:
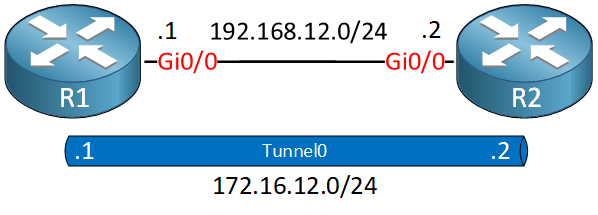
We have two routers with a static tunnel interface. I’m using IOSv Version 15.9(3)M2.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R1
hostname R1
!
ip cef
!
interface GigabitEthernet0/0
ip address 192.168.12.1 255.255.255.0
!
endR2
hostname R2
!
ip cef
!
interface GigabitEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
endR1
Let’s start with R1.
IKEv2
There are four IKEv2 components we need to configure:
- IKEv2 Proposal
- IKEv2 Policy
- IKEv2 Keyring
- IKEv2 Profile
IKEv2 Proposal
The proposal is a collection of items we use in the negotiation of the IKEv2 security association (SA). Let’s configure one:
R1(config)#crypto ikev2 proposal IKEV2_PROPOSAL
R1(config-ikev2-proposal)#encryption aes-cbc-256
R1(config-ikev2-proposal)#group 15
R1(config-ikev2-proposal)#integrity sha256IKEv2 Policy
We also need an IKEv2 policy. This policy contains proposals we want to use in the negotiation. We create a new policy and refer to the proposal we just created:
R1(config)#crypto ikev2 policy IKEV2_POLICY
R1(config-ikev2-policy)#proposal IKEV2_PROPOSALIKEv2 Keyring
We need a keyring that contains the pre-shared key(s) we want to use.
R1(config)#crypto ikev2 keyring IKEV2_KEYRING
R1(config-ikev2-keyring)#peer R2
R1(config-ikev2-keyring-peer)#address 192.168.12.2
R1(config-ikev2-keyring-peer)#pre-shared-key local CISCO
R1(config-ikev2-keyring-peer)#pre-shared-key remote CISCOIKEv2 Profile
In the IKEv2 profile, we configure the local and remote identity and the authentication we want to use. This is where we refer to the keyring we created:
R1(config)#crypto ikev2 profile IKEV2_PROFILE
R1(config-ikev2-profile)#match identity remote fqdn R2.NWL.LAB
R1(config-ikev2-profile)#identity local fqdn R1.NWL.LAB
R1(config-ikev2-profile)#authentication local pre-share
R1(config-ikev2-profile)#authentication remote pre-share
R1(config-ikev2-profile)#keyring local IKEV2_KEYRINGThis completes our IKEv2 configuration on R1.
IPSec
Next up is IPSec.
IPSec Transform-Set
The transform-set is where we configure the encryption and hashing algorithms we want to use:
R1(config)#crypto ipsec transform-set IPSEC_TRANSFORM_SET esp-aes 256 esp-sha256-hmacIPSec Profile
The second part of the IPSec configuration is the profile. This is where we combine the IKEv2 profile and our IPSec transform-set:
R1(config)#crypto ipsec profile IPSEC_PROFILE
R1(ipsec-profile)#set ikev2-profile IKEV2_PROFILE
R1(ipsec-profile)#set transform-set IPSEC_TRANSFORM_SETThis completes the IPSec configuration.
Tunnel Interface
The last part of our site-to-site configuration is the tunnel interface. This is where we attach the IPSec profile:
R1(config)#interface tunnel 0
R1(config-if)#ip address 172.16.12.1 255.255.255.0
R1(config-if)#tunnel source gigabitEthernet 0/0
R1(config-if)#tunnel destination 192.168.12.2
R1(config-if)#tunnel protection ipsec profile IPSEC_PROFILEAnd that wraps up our VPN configuration on R1.
R2
We’ll do the exact same thing on R2. Here are all the commands:
R2(config)#crypto ikev2 proposal IKEV2_PROPOSAL
R2(config-ikev2-proposal)#encryption aes-cbc-256
R2(config-ikev2-proposal)#integrity sha256
R2(config-ikev2-proposal)#group 15
R2(config)#crypto ikev2 policy IKEV2_POLICY
R2(config-ikev2-policy)#proposal IKEV2_PROPOSAL
R2(config)#crypto ikev2 keyring IKEV2_KEYRING
R2(config-ikev2-keyring)#peer R1
R2(config-ikev2-keyring-peer)#address 192.168.12.1
R2(config-ikev2-keyring-peer)#pre-shared-key local CISCO
R2(config-ikev2-keyring-peer)#pre-shared-key remote CISCO
R2(config)#crypto ikev2 profile IKEV2_PROFILE
R2(config-ikev2-profile)#match identity remote fqdn R1.NWL.LAB
R2(config-ikev2-profile)#identity local fqdn R2.NWL.LAB
R2(config-ikev2-profile)#authentication remote pre-share
R2(config-ikev2-profile)#authentication local pre-share
R2(config-ikev2-profile)#keyring local IKEV2_KEYRING
R2(config)#crypto ipsec transform-set IPSEC_TRANSFORM_SET esp-aes 256 esp-sha256-hmac
R2(config)#crypto ipsec profile IPSEC_PROFILE
R2(ipsec-profile)#set transform-set IPSEC_TRANSFORM_SET
R2(ipsec-profile)#set ikev2-profile IKEV2_PROFILE
R2(config)#interface Tunnel0
R2(config-if)#ip address 172.16.12.2 255.255.255.0
R2(config-if)#tunnel source GigabitEthernet0/0
R2(config-if)#tunnel destination 192.168.12.1
R2(config-if)#tunnel protection ipsec profile IPSEC_PROFILEThat’s all we need.
Disable Smart Defaults
Optionally, you can disable the smart defaults if you want. Since we configure everything manually, you might have a good reason not to use smart defaults. You can disable them by adding no in front of them:
R1 & R2
(config)#no crypto ikev2 policy default
(config)#no crypto ipsec profile default
(config)#no crypto ipsec transform-set default
(config)#no crypto ikev2 proposal defaultWhen you disable a default, it loses all user configuration. You can re-enable a default by using the command again. For example: crypto ikev2 proposal default will re-enable the default IKEv2 proposal and restores the default values.
Verification
Let’s verify our work. First, I send some pings to the other end of the tunnel to trigger our VPN:
R1#ping 172.16.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/7 msOur pings are working, but to be sure let’s try some IKEv2 and IPSec show commands.
IKEv2
Let’s check out our IKEv2 policy:
R1#show crypto ikev2 policy
IKEv2 policy : IKEV2_POLICY
Match fvrf : global
Match address local : any
Proposal : IKEV2_PROPOSAL
IKEv2 policy : default DisabledThis tells me the name of our policy and the proposal it uses, and it also shows us that the default policy is disabled. Let’s take a closer look at our proposal:
R1#show crypto ikev2 proposal
IKEv2 proposal: IKEV2_PROPOSAL
Encryption : AES-CBC-256
Integrity : SHA256
PRF : SHA256
DH Group : DH_GROUP_3072_MODP/Group 15
IKEv2 proposal: default DisabledAbove, we see our proposal and it also tells us that the default proposal is disabled. Let’s check our profile:
R1#show crypto ikev2 profile
IKEv2 profile: IKEV2_PROFILE
Ref Count: 5
Match criteria:
Fvrf: global
Local address/interface: none
Identities:
fqdn R2.NWL.LAB
Certificate maps: none
Local identity: fqdn R1.NWL.LAB
Remote identity: none
Local authentication method: pre-share
Remote authentication method(s): pre-share
EAP options: none
Keyring: IKEV2_KEYRING
Trustpoint(s): none
Lifetime: 86400 seconds
DPD: disabled
NAT-keepalive: disabled
Ivrf: none
Virtual-template: none
mode auto: none
AAA AnyConnect EAP authentication mlist: none
AAA EAP authentication mlist: none
AAA Accounting: none
AAA group authorization: none
AAA user authorization: noneThe output above gives us an overview of the identities and keyring we use. Now to the important part; do we have an SA?
R1#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.12.1/500 192.168.12.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:15, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/879 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: 40BFB27B5A1863C2 Remote spi: E894779083360034
Local id: R1.NWL.LAB
Remote id: R2.NWL.LAB
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : No
IPv6 Crypto IKEv2 SAExcellent. We have an IKEv2 SA. You can also use this command which gives a similar output:
R1#show crypto ikev2 session detailed
IPv4 Crypto IKEv2 Session
Session-id:1, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.12.1/500 192.168.12.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:15, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/896 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: 40BFB27B5A1863C2 Remote spi: E894779083360034
Local id: R1.NWL.LAB
Remote id: R2.NWL.LAB
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : No
Child sa: local selector 192.168.12.1/0 - 192.168.12.1/65535
remote selector 192.168.12.2/0 - 192.168.12.2/65535
ESP spi in/out: 0xF653765B/0xD480A04F
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA256
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
IPv6 Crypto IKEv2 SessionWhen it comes to IKEv2, everything looks good.
IPSec
Let’s dive into IPSec. We’ll check our profile:



Hello Ravi
That’s a great question. I’ll do my best to break it down and explain.
The relationship between IPsec tunnel mode under the transform-set configuration and the tunnel interface mode on Cisco routers involves two distinct but interconnected concepts.
IPsec Tunnel Mode refers to how IPsec processes packets. In this mode, the entire original IP packet is encapsulated with a new IP header. This approach is commonly used to secure traffic between different networks or gateways, effectively creating a logical tunnel. When configuring IPsec protection on a
... Continue reading in our forum