Lesson Contents
FlexVPN is Cisco’s implementation of IPSec VPN with IKEv2. With smart defaults, it automatically uses pre-configured values for the IKEv2 proposal and policy, and the IPSec transform-set and profile. The only items left to configure are the IKEv2 profile and keyring. The values it uses are based on Cisco’s best practices. This simplifies the configuration.
In this lesson, we configure a FlexVPN site-to-site VPN between two routers using smart defaults. We’ll create the keyring for authentication, build the IKEv2 profile, configure tunnel interfaces, and verify that encryption works correctly.
What You Will Learn
Here is what we cover:
- Smart defaults eliminate four configuration steps:
- IKEv2 proposal
- IKEv2 policy
- IPSec transform-set
- IPSec profile
- Only two items require manual configuration:
- IKEv2 keyring (for authentication)
- IKEv2 profile (for identity matching)
- Default encryption standards are production-ready
We will look at the configuration and how to verify our work.
Prerequisites
Before starting this lesson, you should be familiar with FlexVPN. You can learn more in the introduction to FlexVPN lesson.
Explanation
A VPN with IKEv2 requires the following items:
- IKEv2:
- IKEv2 proposal
- IKEv2 policy
- IKEv2 profile
- IKEv2 keyring
- IPSec:
- IPSec transform-set
- IPSec profile
Smart defaults let you use pre-defined values based on best practices for everything except the following two items:
- IKEv2 profile
- IKEv2 keyring
That means we don’t have to configure these items:
- IKEv2 proposal
- IKEv2 policy
- IPSec transform-set
- IPSec profile
In this lesson, I’ll show you how to configure FlexVPN site-to-site between two routers using smart defaults. We also have a lesson where we do the exact same thing, except without smart defaults.
Configuration
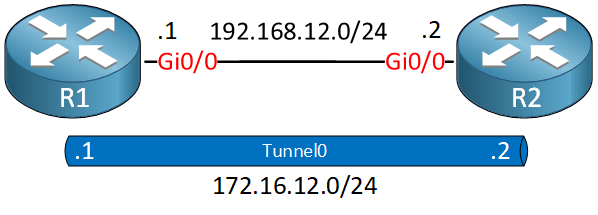
This is the topology we are going to use:
We have two routers. On each router, we configure a static tunnel interface that we use for our FlexVPN site-to-site connection. I’m using IOSv Version 15.9(3)M2. There are three items we need to configure:
-
- IKEv2 keyring.
- IKEv2 profile.
- Tunnel interface.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R1
hostname R1
!
ip cef
!
interface GigabitEthernet0/0
ip address 192.168.12.1 255.255.255.0
!
endR2
hostname R2
!
ip cef
!
interface GigabitEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
endI’ll walk you through the different components one by one.
R1
Let’s start with R1.
Keyring
First, we configure a keyring. This is where we specify the pre-shared keys we want to use with the remote router:
R1(config)#crypto ikev2 keyring KEYRING
R1(config-ikev2-keyring)#peer R2
R1(config-ikev2-keyring-peer)#address 192.168.12.2
R1(config-ikev2-keyring-peer)#pre-shared-key local CISCO
R1(config-ikev2-keyring-peer)#pre-shared-key remote CISCOIKEv2 Profile
Now we can create an IKEv2 profile. This is where we configure the identities of our routers, the authentication we want to use, and the keyring we want to use:
R1(config)#crypto ikev2 profile default
R1(config-ikev2-profile)#match identity remote fqdn R2.NWL.LAB
R1(config-ikev2-profile)#identity local fqdn R1.NWL.LAB
R1(config-ikev2-profile)#authentication local pre-share
R1(config-ikev2-profile)#authentication remote pre-share
R1(config-ikev2-profile)#keyring local KEYRINGIn the configuration above, I picked the name “default”. There is no default IKEv2 profile on the router but I do this for a reason. The default IPSec profile is configured to use an IKEv2 profile named “default”. I’ll show you this when we verify our configuration.
Tunnel
The last item to configure is a tunnel interface. We create one and add the default IPSec profile here:
R1(config)#interface Tunnel 0
R1(config-if)#ip address 172.16.12.1 255.255.255.0
R1(config-if)#tunnel source gigabitEthernet 0/0
R1(config-if)#tunnel destination 192.168.12.2
R1(config-if)#tunnel protection ipsec profile defaultThis completes our configuration on R1.
R2
Let’s do the exact same thing on R2:
R2(config)#crypto ikev2 keyring KEYRING
R2(config-ikev2-keyring)# peer R1
R2(config-ikev2-keyring-peer)#address 192.168.12.1
R2(config-ikev2-keyring-peer)#pre-shared-key local CISCO
R2(config-ikev2-keyring-peer)#pre-shared-key remote CISCOR2(config)#crypto ikev2 profile default
R2(config-ikev2-profile)#match identity remote fqdn R1.NWL.LAB
R2(config-ikev2-profile)#identity local fqdn R2.NWL.LAB
R2(config-ikev2-profile)#authentication remote pre-share
R2(config-ikev2-profile)#authentication local pre-share
R2(config-ikev2-profile)#keyring local KEYRINGR2(config)#interface Tunnel0
R2(config-if)#ip address 172.16.12.2 255.255.255.0
R2(config-if)#tunnel source GigabitEthernet0/0
R2(config-if)#tunnel destination 192.168.12.1
R2(config-if)#tunnel protection ipsec profile defaultThis completes our configuration on both routers.
Verification
Let’s figure out whether our site-to-site VPN works. I’ll send a ping between the tunnel interfaces to trigger the VPN:
R1#ping 172.16.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 msOur ping works, but that doesn’t prove much. Let’s continue and check everything.
IKEv2
Let’s take a look at the default IKEv2 policy:
R1#show crypto ikev2 policy
IKEv2 policy : default
Match fvrf : any
Match address local : any
Proposal : defaultIn the output above, we see that the IKEv2 policy uses the default IKEv2 proposal. Let’s take a look at that:
R1#show crypto ikev2 proposal
IKEv2 proposal: default
Encryption : AES-CBC-256 AES-CBC-192 AES-CBC-128
Integrity : SHA512 SHA384 SHA256 SHA96 MD596
PRF : SHA512 SHA384 SHA256 SHA1 MD5
DH Group : DH_GROUP_1536_MODP/Group 5 DH_GROUP_1024_MODP/Group 2And let’s check the IKEv2 profile that we configured:
R1#show crypto ikev2 profile
IKEv2 profile: default
Ref Count: 5
Match criteria:
Fvrf: global
Local address/interface: none
Identities:
fqdn R2.NWL.LAB
Certificate maps: none
Local identity: fqdn R1.NWL.LAB
Remote identity: none
Local authentication method: pre-share
Remote authentication method(s): pre-share
EAP options: none
Keyring: KEYRING
Trustpoint(s): none
Lifetime: 86400 seconds
DPD: disabled
NAT-keepalive: disabled
Ivrf: none
Virtual-template: none
mode auto: none
AAA AnyConnect EAP authentication mlist: none
AAA EAP authentication mlist: none
AAA Accounting: none
AAA group authorization: none
AAA user authorization: noneDo we have a Security Association (SA)? Let’s find out:
R1#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.12.1/500 192.168.12.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2074 sec
CE id: 1034, Session-id: 22
Status Description: Negotiation done
Local spi: C403D41F6A568C36 Remote spi: 554A2F783C96DA45
Local id: R1.NWL.LAB
Remote id: R2.NWL.LAB
Local req msg id: 2 Remote req msg id: 0
Local next msg id: 2 Remote next msg id: 0
Local req queued: 2 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
IPv6 Crypto IKEv2 SAWe do have an IKEv2 SA. There is one more command that gives a similar output:



Hello Byorn
The
peer xxxxcommand is used to define the peer to peer group. It is a word you use to define that group. You can choose whatever you want. In the following lesson, Rene chooses to use “R2” which is the name of the remote router to which he is connecting. Take a look at this lesson which describes FlxeVPN site to site configurations:https://networklessons.com/vpn/flexvpn-site-to-site-smart-defaults
I hope this has been helpful!
Laz
The ikev2profile kind of came out of left field with this:
There’s been no mention of dns or a dns server, unless I missed it, no discussion about configuring the ip-domain-lookup functionality. Does Cisco just assume you can put in any fqdn and it just works? Up to this point it’s just been ip addresses…
Hello William
You’re right, it is confusing! I believe the source of the confusion comes from the use of the
fqdnkeyword.The use of FQDNs in IKEv2 profiles doesn’t require DNS resolution because these FQDN values simply serve as static identifiers rather than actual DNS queries.
The
... Continue reading in our forummatch identity remote fqdncommand compares the peer’s declared identity against a preconfigured string. Peers exchange identities during IKEv2 negotiation as raw strings, not IP addresses. This FQDN value simply acts as an authentication fingerprint. Both devices must have matcVery helpful! Thanks