Lesson Contents
With FlexVPN, we have two options for routing:
- Use a dynamic routing protocol like EIGRP, OSPF, or BGP.
- Advertise routes within the IKEv2 Security Association (SA).
In this lesson, I’ll explain how to advertise routes with IKEv2.
Configuration
This is the topology we are going to use:
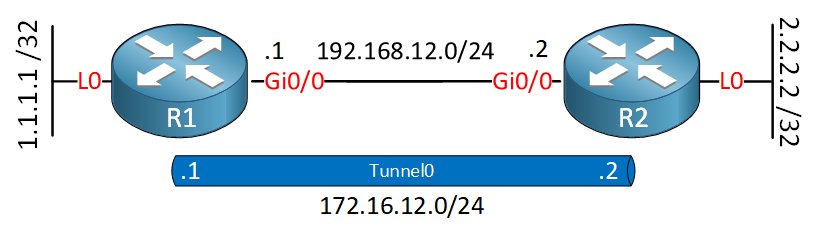
I’m using the same topology and configuration which we used in the FlexVPN site-to-site smart defaults lesson. The only difference is that this time, each router has a loopback interface. We will advertise the networks on these loopback interfaces with IKEv2.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R1
hostname R1
!
ip cef
!
crypto ikev2 keyring KEYRING
peer R2
address 192.168.12.2
pre-shared-key local CISCO
pre-shared-key remote CISCO
!
crypto ikev2 profile default
match identity remote fqdn R2.NWL.LAB
identity local fqdn R1.NWL.LAB
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
!
crypto ipsec profile default
set ikev2-profile default
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Tunnel0
ip address 172.16.12.1 255.255.255.0
tunnel source GigabitEthernet0/0
tunnel destination 192.168.12.2
tunnel protection ipsec profile default
!
interface GigabitEthernet0/0
ip address 192.168.12.1 255.255.255.0
!
endR2
hostname R2
!
ip cef
!
crypto ikev2 keyring KEYRING
peer R1
address 192.168.12.1
pre-shared-key local CISCO
pre-shared-key remote CISCO
!
crypto ikev2 profile default
match identity remote fqdn R1.NWL.LAB
identity local fqdn R2.NWL.LAB
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
!
crypto ipsec profile default
set ikev2-profile default
!
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface Tunnel0
ip address 172.16.12.2 255.255.255.0
tunnel source GigabitEthernet0/0
tunnel destination 192.168.12.1
tunnel protection ipsec profile default
!
interface GigabitEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
endTo configure IKEv2 routing, we need an IKEv2 authorization policy. You can configure this locally on the router or on a RADIUS server. We’ll configure a local policy.
R1
Let’s start with R1. First, we need to enable AAA and create a new AAA authorization list:
R1(config)#aaa new-model
R1(config)#aaa authorization network FLEXVPN_LOCAL localWe need to configure which routes we want to advertise to the other router. We do this by specifying an access-list under the IKEv2 authorization policy:
R1(config)#crypto ikev2 authorization policy default
R1(config-ikev2-author-policy)#route set access-list FLEXVPN_ROUTES
R1(config)#ip access-list standard FLEXVPN_ROUTES
R1(config-std-nacl)#permit host 1.1.1.1The final step is to add the AAA authorization list under the IKEv2 profile:
R1(config)#crypto ikev2 profile default
R1(config-ikev2-profile)#aaa authorization group psk list FLEXVPN_LOCAL defaultThis completes our configuration.
R2
We’ll configure the same thing on R2:
R2(config)#aaa new-model
R2(config)#aaa authorization network FLEXVPN_LOCAL local
R2(config)#crypto ikev2 authorization policy default
R2(config-ikev2-author-policy)#route set access-list FLEXVPN_ROUTES
R2(config)#ip access-list standard FLEXVPN_ROUTES
R2(config-std-nacl)#permit host 2.2.2.2
R2(config)#crypto ikev2 profile default
R2(config-ikev2-profile)#aaa authorization group psk list FLEXVPN_LOCAL defaultThat’s all we need. Let’s verify our work.
Verification
If you already configured FlexVPN, you might want to clear the SA with the clear crypto sa command. When the tunnel is back up, we can check the IKEv2 SA:
R1#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.12.1/500 192.168.12.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/851 sec
CE id: 1060, Session-id: 57
Status Description: Negotiation done
Local spi: 798CFC24798EED13 Remote spi: DF621FC6F730E675
Local id: R1.NWL.LAB
Remote id: R2.NWL.LAB
Local req msg id: 0 Remote req msg id: 3
Local next msg id: 0 Remote next msg id: 3
Local req queued: 0 Remote req queued: 3
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : No
Remote subnets:
172.16.12.2 255.255.255.255
2.2.2.2 255.255.255.255R2#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.12.2/500 192.168.12.1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/884 sec
CE id: 1060, Session-id: 2
Status Description: Negotiation done
Local spi: DF621FC6F730E675 Remote spi: 798CFC24798EED13
Local id: R2.NWL.LAB
Remote id: R1.NWL.LAB
Local req msg id: 3 Remote req msg id: 0
Local next msg id: 3 Remote next msg id: 0
Local req queued: 3 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
Remote subnets:
172.16.12.1 255.255.255.255
1.1.1.1 255.255.255.255In the output of R1 and R2 above, we see two remote subnets on each router:
- One remote subnet for the loopback interface.
- One remote subnet for the remote tunnel IP address.



Hello Ravi
FlexVPN tunnel interfaces typically use GRE over IPsec. This means the router first encapsulates packets in a GRE header, then encrypts them with IPsec.
When you specify
tunnel mode ipsec ipv4without GRE, the tunnel becomes a pure IPsec interface or a VTI. FlexVPN supports this configuration mode, and can indeed function using IKEv2 routing as well, but you need to add some additional changes.You must use a transform set ACL or Crypto Map ACL that permits traffic. Even though you’re using a profile (and not classic crypto maps), IPsec still requir
... Continue reading in our forum