Lesson Contents
Port security is a feature on Cisco switches that checks and limits which MAC addresses are allowed on a switchport. By default, there is no limit to the number of MAC addresses a switch can learn on an interface, and all MAC addresses are allowed. This can be a security risk when users connect unauthorized devices like other switches or access points.
In this lesson, you will learn how to configure port security to restrict the number of MAC addresses per port, specify which MAC addresses are allowed, and control what happens when violations occur.
Key Takeaways
- Port security limits the number of MAC addresses allowed on a switchport
- You can manually specify allowed MAC addresses or use sticky learning to automatically learn MAC addresses
- Three violation modes exist:
- shutdown (err-disables port)
- restrict (drops frames + logs)
- protect (drops frames silently)
- Shutdown mode puts the interface in err-disable state and requires manual recovery or automatic recovery with
errdisable recovery - The default recovery timer is 300 seconds (5 minutes), but it can be modified
Prerequisites
To understand port security, you should be familiar with how switches learn MAC addresses.
Configuration
Let’s take a look at the following situation:
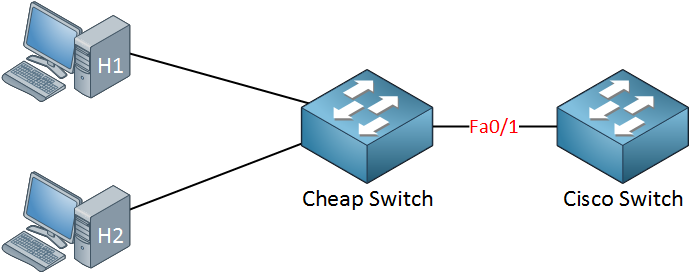
In the topology above, someone connected a cheap (unmanaged) switch that they brought from home to the FastEthernet 0/1 interface of our Cisco switch. Sometimes people like to bring an extra switch from home to the office. As a result, our Cisco switch will learn the MAC address of H1 and H2 on its FastEthernet 0/1 interface.
Of course, we don’t want people to bring their own switches and connect them to our network, so we want to prevent this from happening. This is how we can do it:
Switch(config)#interface fa0/1 Switch(config-if)#switchport port-security Switch(config-if)#switchport port-security maximum 1
Use the switchport port-security command to enable port security. I have configured port security, so only one MAC address is allowed. Once the switch sees another MAC address on the interface, it will be in violation, and something will happen. I’ll show you what happens in a bit…
Besides setting a maximum on the number of MAC addresses, we can also use port security to filter MAC addresses. You can use this to only allow specific MAC addresses. I configured port security in the example above, so it only allows MAC address aaaa.bbbb.cccc. This is not the MAC address of my computer, so it’s perfect for demonstrating a violation.
Switch(config)#interface fa0/1 Switch(config-if)#switchport port-security mac-address aaaa.bbbb.cccc
Use the switchport port-security mac-address command to define the MAC address that you want to allow. Now we’ll generate some traffic to cause a violation:
C:\Documents and Settings\H1>ping 1.2.3.4
I’m pinging to some bogus IP address…there is nothing with IP address 1.2.3.4; I just want to generate some traffic. Here’s what you will see:
SwitchA# %PM-4-ERR_DISABLE: psecure-violation error detected on Fa0/1, putting Fa0/1 in err-disable state %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 0090.cc0e.5023 on port FastEthernet0/1. %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to down
We have a security violation, and as a result, the port goes in err-disable state. As you can see, it is now down. Let’s take a closer look at port security:
Switch#show port-security interface fa0/1 Port Security : Enabled Port Status : Secure-shutdown Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0090.cc0e.5023:1 Security Violation Count : 1
Here is a useful command to check your port security configuration. Use show port-security interface to see the port security details per interface. You can see the violation mode is shutdown and that the last violation was caused by MAC address 0090.cc0e.5023 (H1).
Switch#show interfaces fa0/1
FastEthernet0/1 is down, line protocol is down (err-disabled)
Shutting the interface after a security violation is a good idea (security-wise), but the problem is that the interface will stay in err-disable state. This probably means another call to the helpdesk and you bringing the interface back to the land of the living! Let’s activate it again:
Switch(config)#interface fa0/1 Switch(config-if)#shutdown Switch(config-if)#no shutdown
To get the interface out of the err-disable state, you need to type “shutdown” followed by “no shutdown.” Only typing “no shutdown” is not enough!
It might be easier if the interface could recover itself after a certain time. You can enable this with the following command:



Hi, your lessons are very interesting. Thank’s.
Hi Rene, thanks for the lessons. Very interesting and informative - keep up the good work
Instead of reading 1253 pdf’s from Cisco in 10min everything was understood with simple and interesting examples. Gongratulations René, here it is a very useful lesson.
Thanks Luís! Glad to hear it was useful to you.
Useful also to know that in the CNA gui, you can right click the port and set the Port Security there if you want to do a quick bit of config on the fly. Thanks