Lesson Contents
The ARP (Address Resolution Protocol) is used to find the MAC address of any IP address that you are trying to reach on your local network, it’s a simple protocol and vulnerable to an attack called ARP poisoning (or ARP spoofing).
ARP poisoning is an attack where we send fake ARP reply packets on the network. There are two possible attacks:
- MITM (Man in the middle): the attacker will send an ARP reply with its own MAC address and the IP address of a legitimate host, server or router. When the victim receives the ARP reply it will update its ARP table. When it tries to reach the legitimate device, the IP packets will end up at the attacker.
- DOS (Denial of Service): the attacker will send many ARP replies with the MAC address of a legitimate server. All devices in the network will update their ARP tables and all IP packets in the network will be sent to the server, overloading it with traffic.
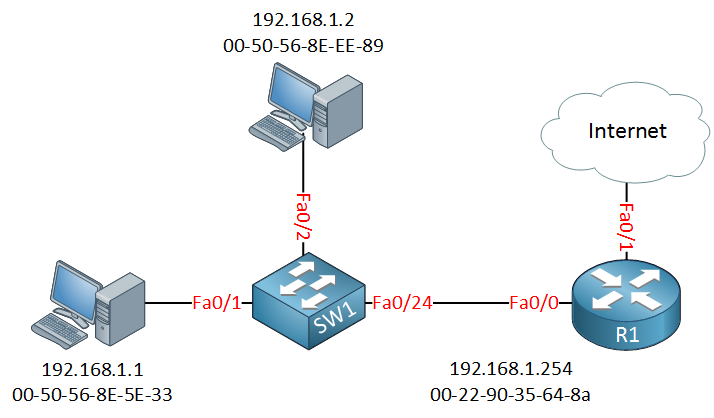
In this lesson we’ll take a look at a MITM attack performed through ARP poisoning, to demonstrate this we’ll use the following topology:
Above we have a switch that connects two computers and a router, which is used for Internet access. The computer on the left side is a Windows computer with a user browsing the Internet, the computer on the top is our attacker.
Traffic Pattern without ARP Poisoning
Let’s take a look at the MAC addresses and ARP tables of the host on the left side (192.168.1.1) and the router:
C:\Users\host1>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : vmware
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82574L Gigabit Network Connection
Physical Address. . . . . . . . . : 00-50-56-8E-5E-33
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::e8b4:ac21:751f:fa34%12(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.1.1(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Tuesday, October 6, 2015 1:46:34 AM
Lease Expires . . . . . . . . . . : Wednesday, October 7, 2015 2:02:04 AM
Default Gateway . . . . . . . . . : 192.168.1.254
DHCP Server . . . . . . . . . . . : 192.168.1.254
DHCPv6 IAID . . . . . . . . . . . : 251678806
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-1D-13-64-E8-00-50-56-8E-5E-33
DNS Servers . . . . . . . . . . . : 8.8.8.8
NetBIOS over Tcpip. . . . . . . . : EnabledAbove you can see the MAC address and IP address of the host on the left side, this is a Windows 8 computer. The default gateway is 192.168.1.254 (R1). Here’s the ARP table:
C:\Users\host1>arp -a
Interface: 192.168.1.1 --- 0xc
Internet Address Physical Address Type
192.168.1.254 00-22-90-35-64-8a dynamicThe output above is the IP address and MAC address of the router. We can verify the MAC address of the router like this:
R1#show interfaces FastEthernet 0/0 | include bia
Hardware is Gt96k FE, address is 0022.9035.648a (bia 0022.9035.648a)And here’s the ARP table of the router with an entry for the host on the left side:
R1#show ip arp | include 192.168.1.1
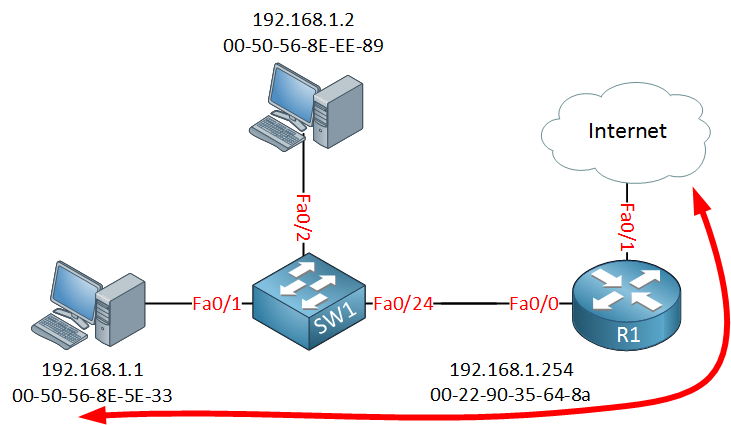
Internet 192.168.1.1 8 0050.568e.5e33 ARPA FastEthernet0/0This is how it should be, our traffic pattern looks like this:
Now let’s see what happens when we perform an ARP poisoning attack…
Traffic Pattern with ARP Poisoning
There are a number of tools you can use for ARP poisoning, I decided to use Kali which is a great Linux distribution with plenty of security tools. Kali comes with an application called Ettercap which offers a couple of MITM (Man in the Middle) attacks.
I will launch Ettercap on the host with IP address 192.168.1.2. Before we launch Ettercap, there’s a couple of configuration changes we have to make. First open the etter.conf file:
# vim /etc/ettercap/etter.confNow change the “ec_uid” and “ec_gid” values to 0:
[privs]
ec_uid = 0
ec_gid = 0These values allow Ettercap to get root access which is required to open network sockets. Also make sure that you have the following two rules in your etter.conf file:
redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"The lines above are required so that Kali will forward IP packets. After saving your changes you can start Ettercap:
# ettercap -GYou will be greeted with the following screen:
Open the “Sniff” menu and select “Unified sniffing”:



Hi Rene,
Very Good Lesson about ARP poisoning and am waiting for DAI.
In real network, can host accepts all the ARP reply from any other host (updates arp table ) without generating the ARP broadcast request for that particular host?
It is very basic question still curious to understand.
Regards,
SV
Hi SV,
You are welcome, the DAI lesson is now online:
DAI (Dynamic ARP Inspection)
Hosts will accept the ARP reply, even if they didn’t send the ARP request.
Rene
Hi Rene,
Thanks for your all valuable articles , I want to do in the Lab environment but at this moment i don’t have any physical Router and switch , is it possible to do in the GNS3 or any other emulation/simulations software where i can do your all of lab.
Thanks,
Arif
Both GNS3 (free) and VIRL (paid) can be used for almost all simulations. Some minor topics, like Bi-Direction Forwarding Detection, Unidirectional Link Detection, and a few more, don’t work well (BFD will actually crash GNS3!).
GNS3 is easier to use, and less complicated to setup. The downsides are you have to supply your own IOS images, and GNS3’s support for switching is marginal at best. If you want to practice topics related to routing I would recommend it.
VIRL requires a paid yearly subscription, as well as access to 3rd party emulator software (VMWare
... Continue reading in our forumThanks a lot, Rene, you are amazing !