Lesson Contents
The IPv6 PACL (Port Access Control List) is basically a regular IPv6 access-list that is applied to a switchport (L2 interface). They only work inbound.
Configuration
Let’s look at quick example. Here’s the topology we’ll use:
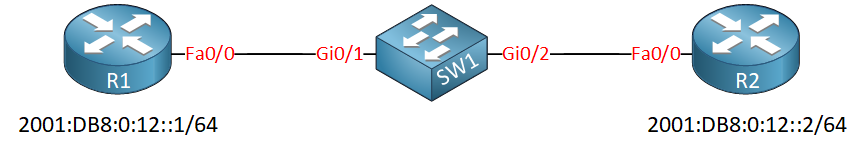
We will use R1 and R2 to generate some IPv6 traffic and on SW1 we’ll configure the PACL.
Let’s configure some IPv6 addresses on R1 and R2:
R1(config)#interface FastEthernet f0/0
R1(config-if)#ipv6 address 2001:DB8:0:12::1/64R2(config)#interface FastEthernet 0/0
R2(config-if)#ipv6 address 2001:DB8:0:12::2/64Let’s enable HTTP server so that we have something to connect to:
R2(config)#ip http serverWithout an ACL, I can connect to the telnet server (enabled by default) and the HTTP server:
R1#telnet 2001:DB8:0:12::2
Trying 2001:DB8:0:12::2 ... OpenR1#telnet 2001:DB8:0:12::2 80
Trying 2001:DB8:0:12::2, 80 ... OpenLet’s create an access-list that denies telnet traffic and permits everything else:
SW1(config)#ipv6 access-list NO_TELNET
SW1(config-ipv6-acl)#deny tcp any host 2001:DB8:0:12::2 eq 23
SW1(config-ipv6-acl)#permit ipv6 any anyWe can see the access-list we created with the show ipv6 access-list command:
SW1#show ipv6 access-list
IPv6 access list NO_TELNET
deny tcp any host 2001:DB8:0:12::2 eq telnet sequence 10
permit ipv6 any any sequence 20Let’s activate the access-list on the GigabitEthernet 0/1 interface that connects to R1:
SW1(config)#interface GigabitEthernet 0/1
SW1(config-if)#ipv6 traffic-filter NO_TELNET inNow, from R1 I’ll try to connect to the telnet and HTTP server on R2:
R1#telnet 2001:DB8:0:12::2
Trying 2001:DB8:0:12::2 ...
% Connection timed out; remote host not respondingR1#telnet 2001:DB8:0:12::2 80
Trying 2001:DB8:0:12::2, 80 ... OpenAs you can see, telnet traffic is no longer permitted.
Unfortunately, hits don’t show in the access-list:
SW1#show ipv6 access-list
IPv6 access list NO_TELNET
deny tcp any host 2001:DB8:0:12::2 eq telnet sequence 10
permit ipv6 any any sequence 20There is the debug ipv6 access-list command but it doesn’t seem to work for PACLs, it only works when you apply an access-list to a routed (L3) interface.


Hello, everyone.
Happy to be the first one to make a post here
I am studying about ACLs for my ENCOR exam and the following piece of information is mentioned in my book:
PACLs have a few restrictions that vary from platform to platform. The following are some
... Continue reading in our forumof the most common restrictions:
Hello David
Indeed some of these restrictions do seem somewhat arbitrary, however there are explanations for each.
- Concerning no outbound filtering support: This has to do with the internal design of a switch, and the ASICs that are used for hardware processing. On a Layer 2 interface, traffic is typically already in the “switching path” once it reaches egress. Applying a PACL on outbound traffic would require the ASIC to re-analyze packets after the forwarding decision has been made, resulting in less efficiency. In general, switches prioritize ingress pro
... Continue reading in our forum