If you ever used fiber cables you might have noticed that there is a different connector to transmit and receive traffic.
If one of the cables (transmit or receive) fails we’ll have a unidirectional link failure and this can cause spanning tree loops. Two protocols can take care of this problem:
- Loop Guard
- UDLD ( Unidirectional Link Detection )
Let’s start by taking a close look at what will happen if we have a unidirectional link failure:
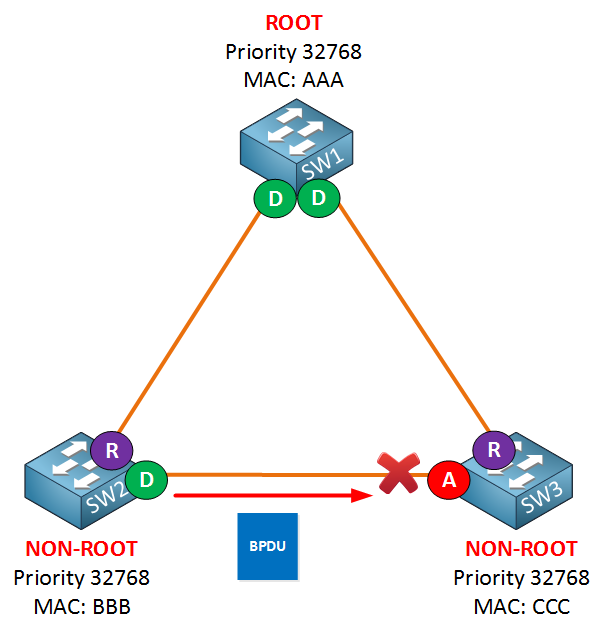
Imagine the links between the switches are fiber links. In reality, there’s a different connector for transmit and receive. SW3 is receiving BPDUs from SW2 and as a result, the interface has become an alternate port and is in blocking mode.
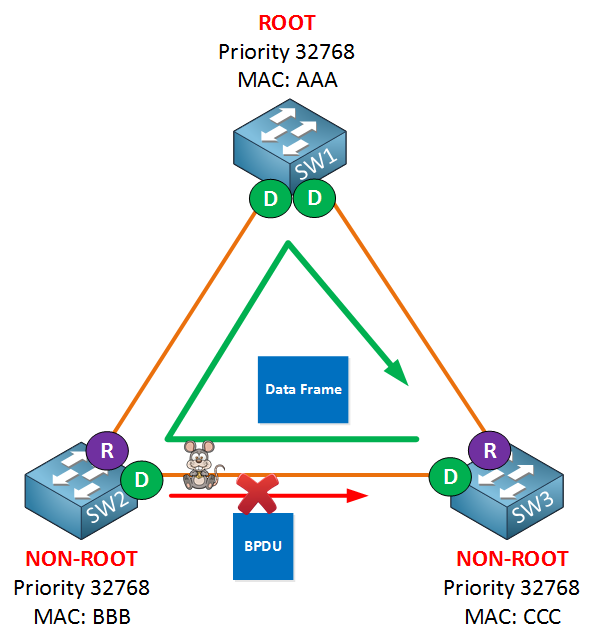
Now something went wrong… mice ate the transmit connector on SW2 towards SW3 and failed due to unknown reasons. As a result, SW3 is not receiving any BPDUs from SW2, but it can still send traffic to SW2.
Because SW3 is not receiving anymore BPDUs on its alternate port it will go into forwarding mode. We now have a one-way loop, as indicated by the green arrow.
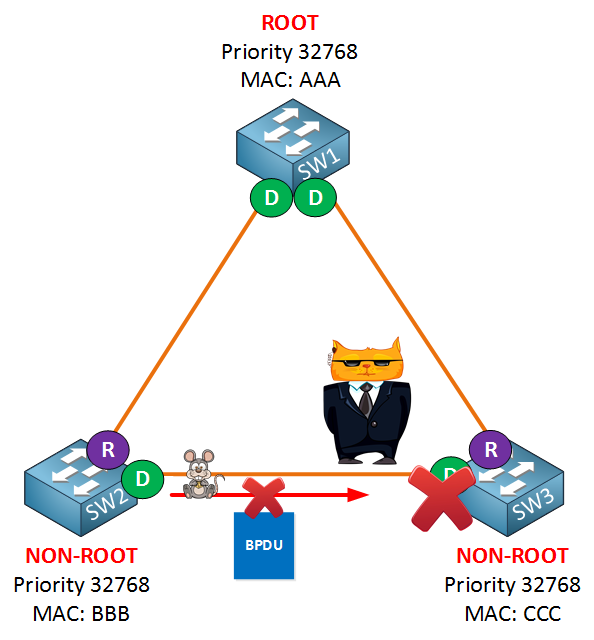
One of the methods we can use to solve our unidirectional link failure is to configure Loop Guard. When a switch is sending but not receiving BPDUs on the interface, Loop Guard will place the interface in the loop-inconsistent state and block all traffic:
Let’s take a look at what this looks like on actual switches. I will use the same topology:
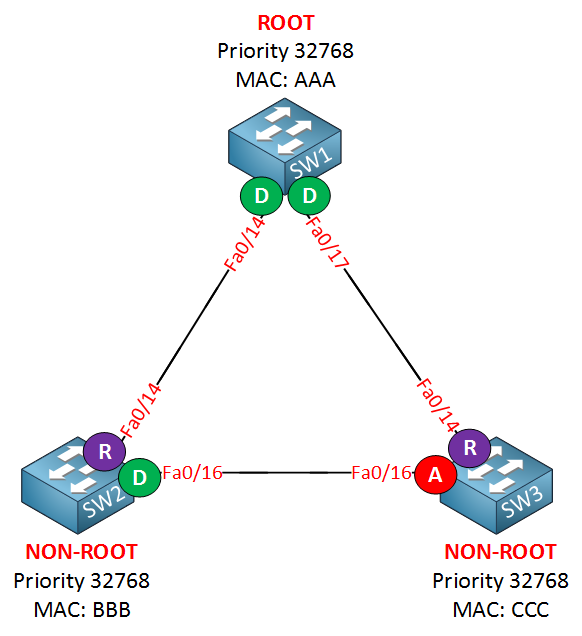
Let’s enable loop guard:
SW1(config)#spanning-tree loopguard defaultSW2(config)#spanning-tree loopguard defaultSW3(config)#spanning-tree loopguard defaultUse the spanning-tree loopguard default command to enable Loop Guard globally. I don’t have any fiber connectors so I’m unable to create a unidirectional link failure. I can simulate it however by using BPDUfilter on SW2’s fa0/16 interface. SW3 won’t receive any BPDUs anymore on its alternate port, which will cause it to go into forwarding mode:
SW2(config)#interface fa0/16
SW2(config-if)#spanning-tree portfast trunk
SW2(config-if)#spanning-tree bpdufilter enableHere’s what will happen:
SW3#
*Mar 1 00:17:14.431: %SPANTREE-2-LOOPGUARD_BLOCK: Loop guard blocking port FastEthernet0/16 on VLAN0001.Normally this would cause a loop, but luckily we have Loop Guard configured. You can see this error message appearing in your console. Problem solved!
Configurations
Want to take a look for yourself? Here, you will find the final configuration of each device.
SW1
hostname SW1
!
spanning-tree loopguard default
!
endSW2
hostname SW2
!
spanning-tree loopguard default
!
interface FastEthernet0/16
spanning-tree portfast trunk
spanning-tree bpdufilter enable
!
endSW3
hostname SW3
!
spanning-tree loopguard default
!
endIf you want, you don’t have to configure Loop Guard globally; you can also do it on the interface level like this:
SW3(config-if)#spanning-tree guard loopThe other protocol we can use to deal with unidirectional link failures is called UDLD (UniDirectional Link Detection). This protocol is not part of the spanning tree toolkit, but it does help us to prevent loops.
Simply said UDLD is a layer 2 protocol that works like a keepalive mechanism. You send hello messages, you receive them, and life is good. As soon as you still send hello messages but don’t receive them anymore, you know something is wrong, and we’ll block the interface.
Let’s use the same topology but configure UDLD this time. Don’t forget to get rid of loop guard first…

SW1(config)#udld ?
aggressive Enable UDLD protocol in aggressive mode on fiber ports except
where locally configured
enable Enable UDLD protocol on fiber ports except where locally
configured
message Set UDLD message parametersThere are multiple methods you can configure UDLD. You can do it globally with the udld command, but this will only activate UDLD for fiber links!




great, tnx for this topic
question, do them work together?
or Cisco doesnt approve to enable them together?
also does them proprietary?
Because there is overlap I personally wouldnt use them togeather. Generally I have seen UDLD used more in the real world but as always..mileage may vary.
Hi Michael
I agree, best not to run both of them at the same time..
Rene