TCP (Transmission Control Protocol) is a reliable transport protocol as it establishes a connection before sending any data and everything that it sends is acknowledged by the receiver. In this lesson we will take a closer look at the TCP header and its different fields. Here’s what it looks like:
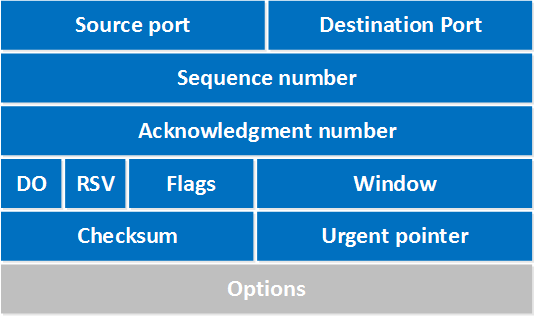
Let’s walk through all these fields:
- Source port: this is a 16 bit field that specifies the port number of the sender.
- Destination port: this is a 16 bit field that specifies the port number of the receiver.
- Sequence number: the sequence number is a 32 bit field that indicates how much data is sent during the TCP session. When you establish a new TCP connection (3 way handshake) then the initial sequence number is a random 32 bit value. The receiver will use this sequence number and sends back an acknowledgment. Protocol analyzers like wireshark will often use a relative sequence number of 0 since it’s easier to read than some high random number.
- Acknowledgment number: this 32 bit field is used by the receiver to request the next TCP segment. This value will be the sequence number incremented by 1.
- DO: this is the 4 bit data offset field, also known as the header length. It indicates the length of the TCP header so that we know where the actual data begins.
- RSV: these are 3 bits for the reserved field. They are unused and are always set to 0.
- Flags: there are 9 bits for flags, we also call them control bits. We use them to establish connections, send data and terminate connections:
- URG: urgent pointer. When this bit is set, the data should be treated as priority over other data.
- ACK: used for the acknowledgment.
- PSH: this is the push function. This tells an application that the data should be transmitted immediately and that we don’t want to wait to fill the entire TCP segment.
- RST: this resets the connection, when you receive this you have to terminate the connection right away. This is only used when there are unrecoverable errors and it’s not a normal way to finish the TCP connection.
- SYN: we use this for the initial three way handshake and it’s used to set the initial sequence number.
- FIN: this finish bit is used to end the TCP connection. TCP is full duplex so both parties will have to use the FIN bit to end the connection. This is the normal method how we end an connection.
- Window: the 16 bit window field specifies how many bytes the receiver is willing to receive. It is used so the receiver can tell the sender that it would like to receive more data than what it is currently receiving. It does so by specifying the number of bytes beyond the sequence number in the acknowledgment field.
- Checksum: 16 bits are used for a checksum to check if the TCP header is OK or not.
- Urgent pointer: these 16 bits are used when the URG bit has been set, the urgent pointer is used to indicate where the urgent data ends.
- Options: this field is optional and can be anywhere between 0 and 320 bits.
To see these fields in action, it’s best to play around with wireshark. Here’s an example of the first part of the TCP three way handshake. I highlighted all the fields:
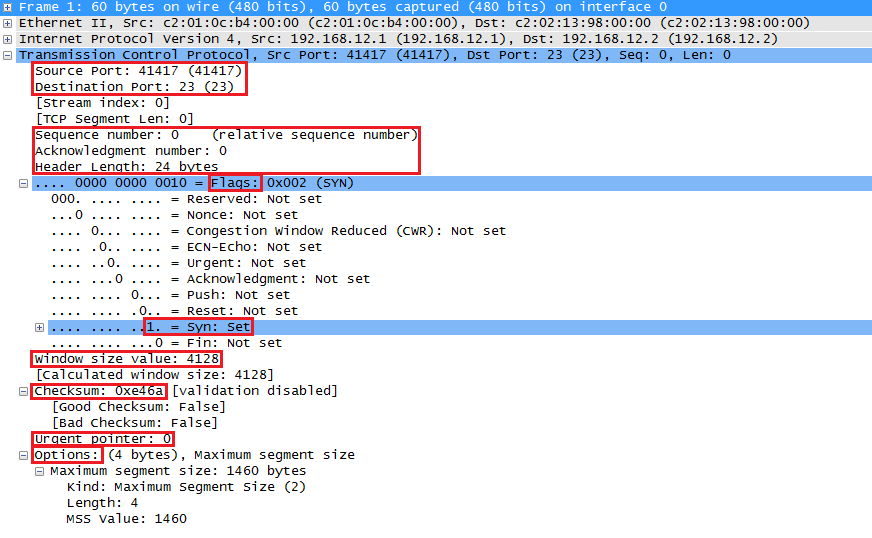
Above you can see the source and destination port. The sequence number is 0 but wireshark tells us that this is a relative sequence number. In reality, it’s something else. You can see the SYN bit has been set in the flags, the window size, checksum, urgent pointer and options.
TCP is a complex protocol but hopefully this lesson has helped to understand what the TCP header looks like. If you have any questions, feel free to leave a comment in our forum.


hi Rene,
I have been trying to use the wireshark to see how this things are but I can’t get there. what can i do?
Hi Yassin,
What exactly is not working for you?
Rene
hi Rene,
Can you please explain this sentence–Sequence number: the sequence number is a 32 bit field that indicates how much data is sent during the TCP session.
Amruta,
This has to do with how the sequence number is incremented during the TCP session. Let’s say Client A is requesting 900 Bytes of data from Server 1. Once Server 1 starts to send the actual data to Client A, the length of the payload of what is being sent directly influences the next sequence number.
So, let’s say the current Sequence number is 1, and the Server sends Client A, 300 Bytes. This means the sequence number will now be 301 (the original sequence number plus the amount of data in the payload that was just sent). Now, let’s say, after Clien
... Continue reading in our forumHi Rene
From what I learned that the maximum size of data that we can send it through one TCP connection = 2^36 = 68719476736 bytes ( Equivalent 68 gigabytes ) and the number 36 came from 32 the seq number filed size plus 4 the DO filed size, please correct me if I wrong.
Best regard
Hussein Samir