Lesson Contents
Cisco Easy VPN is a convenient method to allow remote users to connect to your network using IPsec VPN tunnels. The advantage of Easy VPN is that you don’t have to worry about all the IPSEC security details on the client side. Just configure the remote router, group name, username /password and you are ready to go. In this lesson, I’ll show you how to configure Easy VPN on a Cisco IOS router and we’ll use the Cisco VPN client to setup the connection.
This is the topology that we’ll be using:
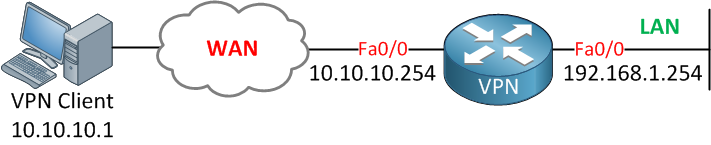
A single router configured for Easy VPN and a computer running Cisco’s VPN client software. Let’s start with the router configuration!
Router Configuration
First, we need to enable AAA for authentication, authorization, and accounting. We can use this for local authentication (usernames and passwords on the router) or use an external RADIUS server for this.
For simplicity, we’ll use local authentication.
VPN(config)#aaa authentication login default local
VPN(config)#aaa authentication login VPNUSER local
VPN(config)#aaa authorization exec default local
VPN(config)#aaa authorization network VPNGROUP localThe username will be “VPNUSER” and we will use a group called “VPNGROUP”. Let’s configure a password for this user:
VPN(config)#username VPNUSER password CISCOOur next move is to configure the IKE policy. This is where you set parameters that are used at the IKE negotiation.
VPN(config)#crypto isakmp policy 1
VPN(config-isakmp)#authentication pre-share
VPN(config-isakmp)#encryption aes
VPN(config-isakmp)#group 2We’ll use AES encryption and diffie hellman group 2. To keep it simple, we’ll use a pre-shared key.
For the VPN group, we’ll have to configure a number of items. First of all, there’s a password, but you can also specify some client-specific parameters like a DNS server, WINS server, how many users are able to connect, etc. Here’s how to do it:
VPN(config)#crypto isakmp client configuration group VPNGROUP
VPN(config-isakmp-group)#key 0 CISCO
VPN(config-isakmp-group)#dns 192.168.1.253
VPN(config-isakmp-group)#wins 192.168.1.253
VPN(config-isakmp-group)#pool VPNPOOL
VPN(config-isakmp-group)#max-users 10
VPN(config-isakmp-group)#netmask 255.255.255.0
VPN(config-isakmp-group)#domain NETWORKLESSONS.LOCALThe VPN group will use “CISCO” as the password and IP address 192.168.1.253 for the DNS and WINS server. The pool name is called VPNPOOL, and this is where we’ll specify the IP addresses for our VPN users:
VPN(config)#ip local pool VPNPOOL 192.168.2.100 192.168.2.200I’m using subnet 192.168.2.100 for VPN users. This is a different subnet from our LAN (192.168.1.0 /24).
The next step is to configure a transform set. This is where we configure our phase 2 authentication and encryption settings:
VPN(config)#crypto ipsec transform-set TRANSFORMSET esp-aes esp-sha-hmacThe transform-set is called “TRANSFORMSET”, and we will use AES encryption and SHA for data origin authentication and integrity protection. Now we’ll configure an ISAKMP profile for our VPN group:
VPN(config)#crypto isakmp profile ISAKMPPROFILE
VPN(conf-isa-prof)#match identity group VPNGROUP
VPN(conf-isa-prof)#client authentication list VPNUSER
VPN(conf-isa-prof)#isakmp authorization list VPNGROUP
VPN(conf-isa-prof)#client configuration address respond
VPN(conf-isa-prof)#virtual-template 1And create a VPN profile that refers to the transform-set and ISAKMP profile that we just created:
VPN(config)#crypto ipsec profile VPNPROFILE
VPN(ipsec-profile)#set transform-set TRANSFORMSET
VPN(ipsec-profile)#set isakmp-profile ISAKMPPROFILELast but not least, we’ll attach the configuration that we did to a virtual interface that receives the connections from the VPN clients. Instead of configuring an IP address on this interface, we’ll tell it to use the IP address of the FastEthernet 0/1 (LAN) interface:



How is easy vpn different from GETVPN?
Hi Edwin,
Normally when you configure IPsec you have to configure security parameters (ESP/AH, DH, encryption algorithm, etc.) on both endpoints. Easy VPN is useful for remote workers so you don’t have to configure all these parameters on the client side. These VPN connections are all point-to-point.
Now imagine you have a large company with a HQ and multiple branch offices. All branch offices should be connected to the HQ and there should be some direct branch-to-branch VPNs. In this case, you really don’t want to configure dozens of these point-to-point VPNs
... Continue reading in our forumHi,
can you make an example using PPTP?
Also let`s say that we have NAT and we are connecting using PPPoE, but on internal LAN we have some servers we want to access from outside, we need to implement static routing?
Thank you
Hi Rene,
How can i use the Easy VPN to tunnel all the traffic from the client PC, not just to reach remote networks?
Especially when VPN router is doing NATing as well.
Traffic will enter and leave the same interface like Hairpin.
Regards,
Bandu
Hi Bandu,
By default, all traffic will be tunneled unless you configure split tunneling.
Rene