Routing protocols can be configured to prevent receiving false routing updates, and EIGRP is no exception. If you don’t use authentication and you are running EIGRP, someone could try to form an EIGRP neighbor adjacency with one of your routers and try to mess with your network…we don’t want that to happen right?
EIGRP supports MD5 authentication and SHA authentication. There is no plaintext authentication.
What does authentication offer us?
- Your router will authenticate the source of each routing update packet it will receive.
- Prevents false routing updates from sources that are not approved.
- Ignore malicious routing updates.
A potential hacker could be sitting on your network with a laptop, booting up a virtual Cisco router and trying the following things:
- Establish a neighbor adjacency with one of your routers and advertise junk routes.
- Send malicious packets and see if you can drop the neighbor adjacency of one of your authorized routers.
Configuration
To configure EIGRP authentication, we need to do the following:
- Configure a key-chain
- Configure a key ID under the key-chain.
- Specify a password for the key ID.
- Optional: specify accept and expire lifetime for the key.
- Configure a key ID under the key-chain.
Let’s use two routers and see if we can configure EIGRP MD5 authentication:
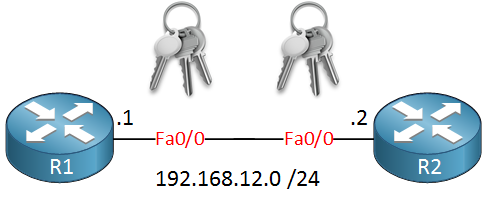
The configuration for both routers is very basic:
R1(config)#interface fastEthernet 0/0
R1(config-if)#ip address 192.168.12.1 255.255.255.0
R1(config)#router eigrp 12
R1(config-router)#network 192.168.12.0R2(config)#interface fastEthernet 0/0
R2(config-if)#ip address 192.168.12.2 255.255.255.0
R2(config)#router eigrp 12
R2(config-router)#network 192.168.12.0The first thing we need to configure is a key-chain:
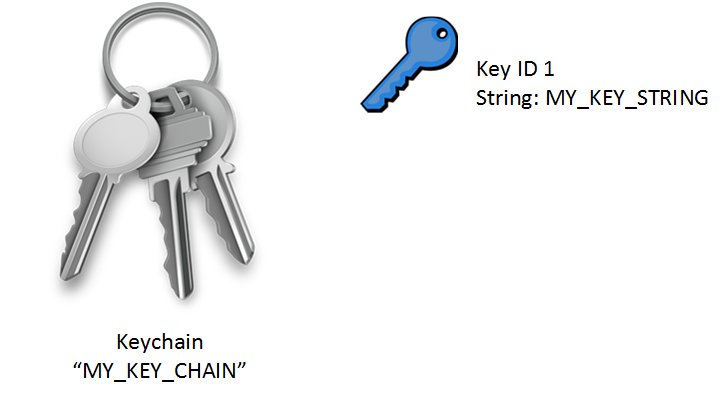
I called mine “MY_KEY_CHAIN,” but it can be different on both routers. It doesn’t matter. The Key ID is a value that has to match on both routers, and the key-string is the password which has to match, of course. This is how to configure a key-chain:
R1(config)#key chain MY_KEY_CHAIN
R1(config-keychain)#key 1
R1(config-keychain-key)#key-string MY_KEY_STRINGR1(config)#interface fastEthernet 0/0
R1(config-if)#ip authentication mode eigrp 12 md5
R1(config-if)#ip authentication key-chain eigrp 12 MY_KEY_CHAINFirst, you must create the key-chain, and then activate it on the interface. The “12” is the AS number of EIGRP. We can enable a debug to see whether authentication is working or not:
R2#debug eigrp packets
EIGRP Packets debugging is on
(UPDATE, REQUEST, QUERY, REPLY, HELLO, IPXSAP, PROBE, ACK, STUB, SIAQUERY, SIAREPLY)
R2# EIGRP: FastEthernet0/0: ignored packet from 192.168.12.1, opcode = 5 (authentication off or key-chain missing)You can check if your configuration is correct by using debug eigrp packets. You can see that we received a packet with MD5 authentication, but I didn’t enable MD5 authentication yet on R2.
Let’s fix that:
R2(config)#key chain MY_KEY_CHAIN
R2(config-keychain)#key 1
R2(config-keychain-key)#key-string MY_KEY_STRING
R2(config)#interface fastEthernet 0/0
R2(config-if)#ip authentication mode eigrp 12 md5
R2(config-if)#ip authentication key-chain eigrp 12 MY_KEY_CHAINRight away, I can see that the EIGRP neighbor adjacency is working:


hello thank you very much. you make CCNA look very easy. you talk me thank you once again
awesome lessons, simple and clearly documented.
I really like the way you explain the things…its simple,clear and easy to understand.
What is an AS number? Thanks.
AS stands for Autonomous System.
An AS is basically a network that falls under one administrative entity. On the Internet we use AS numbers and BGP for routing between autonomous systems. Within an AS, we typically use an IGP like OSPF or EIGRP.
Here’s a list with AS numbers that are used on the Internet:
http://bgp.potaroo.net/cidr/autnums.html
Rene